
Resources

Blog
Preparing for the 2026 World Cup: Security Challenges and How to Tackle Them

Blog
Intel Agents 101: Understand Dataminr’s Groundbreaking Agentic AI Capability

Blog
Billington CyberSecurity Summit 2025: The Transition from Reactive to Proactive Cyber Defense

Blog
Most Common Cyber Threats Targeting Major Events

Blog
Improve Operational Resilience With Dataminr Partnership

Blog
From Alerts to Action: Dataminr’s Agentic AI Powers Real-Time, Actionable Intelligence for SIEM, SOAR, and TIP Systems

Blog
Dataminr Intel Agents Deliver Instant Context for Cyber Threat Intelligence Teams

Blog
Making Sense of Chaos at Black Hat USA 2025

Infographic
Dataminr + Splunk: Supercharge Security with Real-Time Threat Detection and Automation
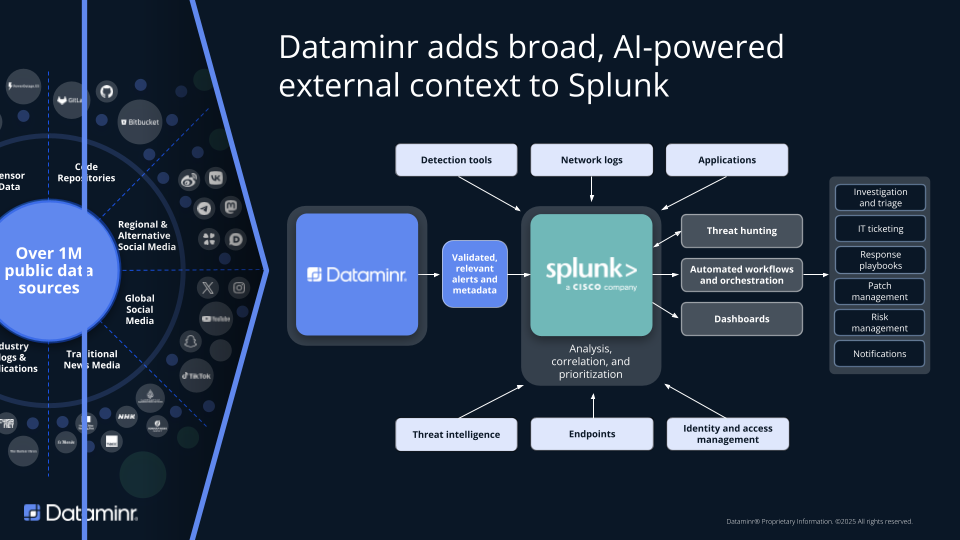
eBook
Supercharge Splunk with Real-Time Threat Intelligence

Insight
Beyond Your Perimeter: Why External Context Is Critical for Security Operations

Blog
Scattered Spider is Wreaking Cyber Havoc. Here’s How to Stay Ahead.

Blog
Tackling AI-Driven Cyber Threats at InfoSecurity Europe 2025

Blog
AI for Preemptive Cyber Defense: Cutting Through the Noise for Greater Efficiencies

On-demand Webinar
Five Ways to Preempt Cyberattacks with Actionable Intelligence

Blog
Building the Next Generation of Risk-Aware Platforms: A Partnership Approach

Blog
From Satellites to Supply Chains: How Real-Time Event Detection Is Transforming Multiple Industries

Insight
2025 Cyberthreat Defense Report: Key Insights
See the power of Dataminr
Get a firsthand look at how our AI platform helps you know first, so you can act faster.
