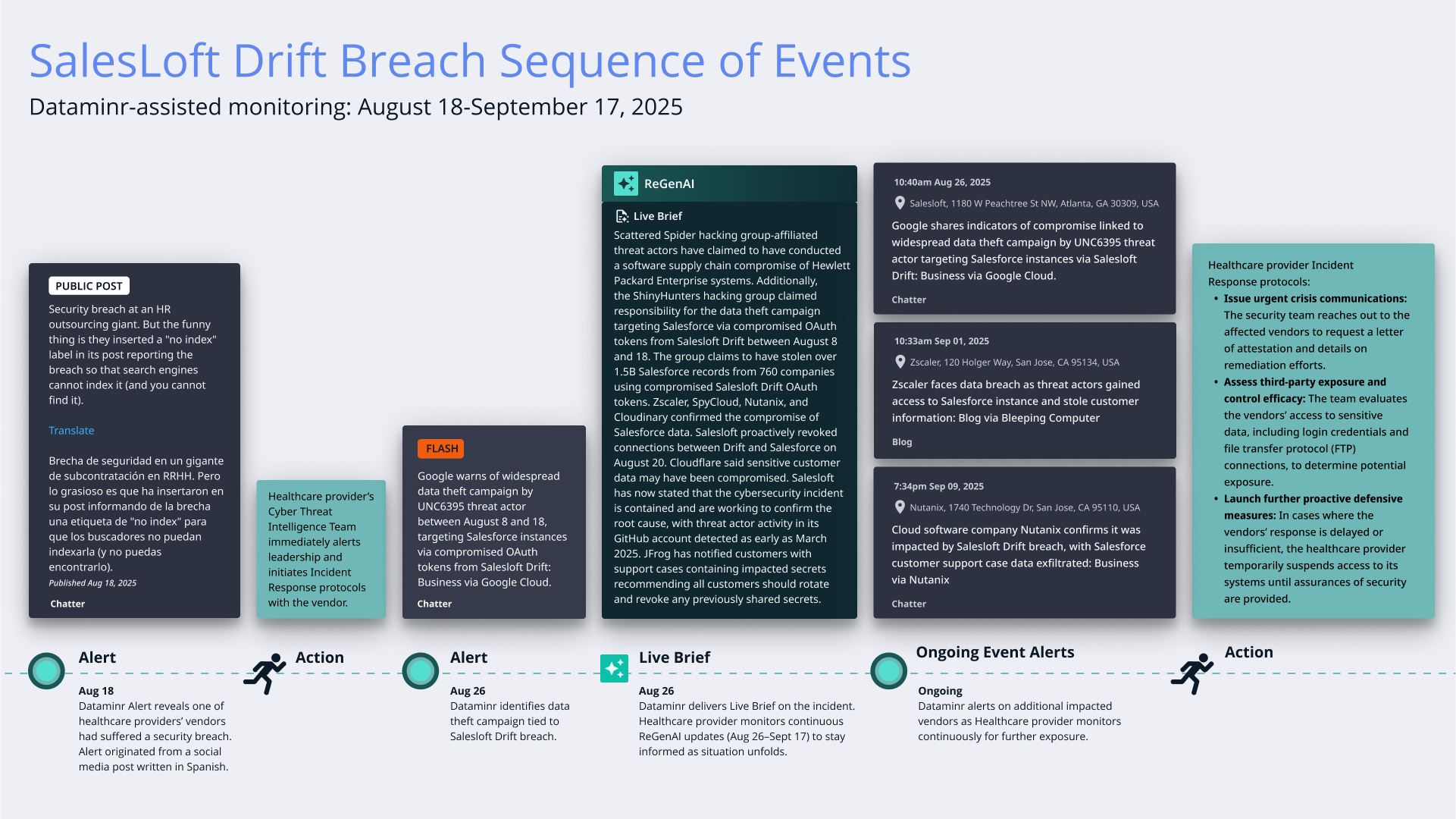
In August 2025, Dataminr identified a potential ransomware attack targeting a Tier 1 vendor of a Fortune 500 healthcare provider. The threat was surfaced via a social media post from a user in Spain. It turned out the Tier 1 vendor was one of many victims affected by the larger Salesloft Drift breach that originated a few days earlier. Dataminr was the first to alert the healthcare provider that one of their vendors was affected.
This early warning, combined with continual, real-time updates provided by Dataminr, provided critical situational awareness for the cybersecurity team at the healthcare provider. The team quickly assessed the validity, severity, and business impact of the attack, and took swift action to harden the organization’s environment and protect its sensitive data.
Although Salesloft, the vendor at the center of the breach, was not directly connected to the healthcare provider, the provider’s cybersecurity team was able to monitor and proactively defend against the ripple effects on its own vendor ecosystem in real time. With hundreds of third-party vendors to track 24/7 across the globe, the team relied on Dataminr for actionable intelligence to safeguard its operations. This proved valuable as news of other organizations affected by the breach emerged.
Using Real-Time Intelligence for Proactive Defense
Days earlier, threat actors UNC6395, purportedly associated with groups Scattered Spider and Shiny Hunters, had manipulated a chatbot integration to access customer data via compromised 0Auth tokens. This breach allowed attackers to access critical systems with private data at some of the most trusted companies in the world, including Workday, Cloudflare, Palo Alto Networks, and Zscaler—organizations known for their robust security measures. The incident highlights the risks of misplaced trust in third-party integrations.
The healthcare provider relied on Dataminr’s real-time intelligence to stay ahead of the unfolding crisis. As alerts about the breach emerged, the security team mobilized immediately and began taking preemptive measures to mitigate the organization’s exposure to the affected third-party vendors, including steps to:
- Issue urgent crisis communications: The security team reached out to the affected vendor to request a letter of attestation and details on remediation efforts.
- Assess third-party exposure and control efficacy: The team evaluated the vendor’s access to sensitive data, including login credentials and file transfer protocol (FTP) connections, to determine potential exposure.
- Launch further proactive defensive measures: In cases where the vendor’s response was delayed or insufficient, the healthcare provider temporarily suspended access to its systems until assurances of security were provided.
The healthcare provider team also used the ongoing information to keep key stakeholders and decision makers across the organization and parent company informed throughout the crisis. They used the incident as an opportunity to educate the wider team about the importance of real-time cyber threat intelligence for third-party risk management. During one presentation to senior company executives, the cybersecurity team explained that the Salesloft Drift breach perfectly exemplifies how a supply chain attack can ripple out to impact even the most secure organizations.
Dataminr’s ability to surface actionable intelligence quickly has proven invaluable to the team. In another instance, when a vendor vulnerability with a CVSS score of 9.9 was identified, Dataminr alerted the team to the critical vulnerability and new threat actor proof-of-concept exploitation of it hours before mainstream media. And some legacy threat intelligence providers missed it altogether. This speed enabled the healthcare provider to notify its parent organization and internal teams before any potential exploitation occurred.
The Dataminr Partnership: Scaling to Real-Time Third-Party Risk Management
Before adopting Dataminr Pulse for Cyber Risk, the healthcare provider’s cybersecurity team faced several core challenges in maintaining accurate, scalable visibility of the external threat landscape and its rapidly expanding third-party ecosystem, including:
- Lack of visibility: The organization struggled to maintain an up-to-date inventory of its vendors and their associated risks.
- Delayed and outdated intelligence: A previous vendor provided point-in-time risk scores without continuous visibility into threats, leaving the team reactive rather than proactive. And before adopting Dataminr, the team got a lot of its information secondhand from its parent company.
- Fragmented processes: Without a centralized source of truth, the security team often relied on disparate tools and manual processes.
Dataminr Pulse for Cyber Risk addressed these pain points by offering an AI-powered platform that delivered real-time alerts and context tailored to the healthcare provider’s needs. Key benefits of the partnership include:
- Scalable, real-time third-party risk monitoring: Dataminr enables the healthcare provider security team to continuously track their more than 300 global third-party vendors, providing a unified view of the organization’s risk landscape.
- Prioritized alerts: Vendors are categorized into low, medium, and high priority tiers, ensuring the security team focuses on the most critical threats.
- Live, continuously updated briefs on attacks: Dataminr provides real-time, proactive, and continuously updated insight into risks as they emerge and evolve.
- Actionable intelligence: Dataminr’s alerts are concise, contextual, and relevant, enabling the team to act quickly without being overwhelmed by noise.
- Multimodal threat detection: Synthesizing text in 150 languages, image, video, audio, and sensor signals across 1M public data sources for comprehensive event, threat, and risk monitoring.
“Dataminr points us in exactly the right direction at the earliest possible time. It saves us hours of investigation time and ensures we’re always aware of what’s happening across our vendor ecosystem.” -Senior Principal Information Security Analyst at the healthcare provider.
Prior to purchasing Dataminr, the team used another solution whose strength was finished reporting. But without the accurate and real-time intelligence to back up the reports, the team found they quickly staled and weren’t adding value.
“We asked ourselves if our finished reporting was actually helping our team: ‘Does it contain relevant IOCs? Is anything actually actionable? Does anybody even talk about it after it’s submitted?’,” questioned a Senior Principal Information Security Analyst at the healthcare provider. “The answer: No, it doesn’t add any value. We need intelligence that our teams can act on. And that’s what we got with Dataminr.”
Integrating Actionable Intelligence into Existing Splunk Workflows
The healthcare provider integrated Dataminr into its existing security stack, including Splunk. This integration has allowed a seamless correlation of Dataminr alerts with existing internal telemetry, further enhancing the organization’s threat detection and response capabilities.
By streamlining existing cybersecurity workflows, the team was able to transform overwhelming streams of both external and internal security signals into highly relevant intelligence that the team could act on in real time. The powerful combination of technologies allows the healthcare provider’s threat intelligence team to stay ahead of AI-powered attackers. The team combines risk-based alerts and advanced security detection in Splunk with Dataminr’s real-time, AI-powered intelligence platform, to surface the earliest signals of cyber threats.
A Model for Preemptive Cybersecurity
The partnership with Dataminr has fundamentally transformed how the healthcare provider manages third-party risk. The cybersecurity team has not only improved response times, but also gained credibility with its parent company by identifying and mitigating threats quickly and effectively. Now, the larger security team of the healthcare provider parent company comes to the healthcare provider’s team for real-time intelligence, rather than the other way around.
“We’ve turned the tables a little bit. Actually, that’s an understatement,” said the Senior Principal Information Security Analyst. “We completely flipped the table over. Now we’re ahead 100% of the time—both in effectiveness and speed. Everybody is very happy with the performance we’ve achieved with Dataminr.”
It’s more important than ever to take proactive cybersecurity measures in today’s interconnected world. For organizations managing complex vendor networks, Dataminr Pulse for Cyber Risk isn’t just a convenience—it’s a necessity.

Demystifying Agentic AI for Cybersecurity Efficiency and Preemptive Defense
In this on-demand session, leading experts from government and industry reveal how agentic AI is revolutionizing cyber defense. Learn to move beyond reactive measures and build a proactive, intelligent security posture that anticipates and neutralizes threats before they strike.
Watch the Webinar