Preempt Breaches with Actionable Vulnerability Intelligence
Situation
An overwhelming flood of vulnerability data and advisories create noise without clarity. You need a solution with actionable vulnerability intelligence so you can get ahead of threats and proactively adapt your defensive posture from the earliest signs of active exposure and exploitation.
Solution
Dataminr processes the broadest scope of public data, applying Multi-Modal Fusion AI, Generative AI, and Agentic AI to identify emerging vulnerabilities and threat activity hidden in terabytes of daily text, audio, imagery, video, and sensor data in 150 languages worldwide.
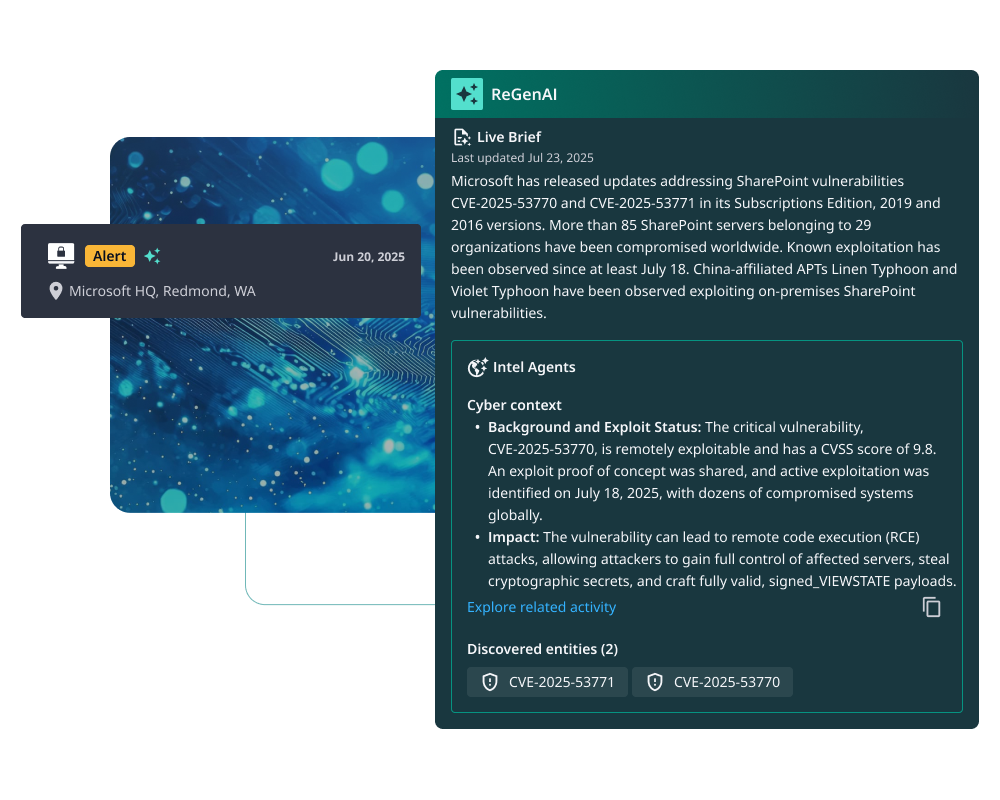
Evaluate New Exposures at Machine Speed
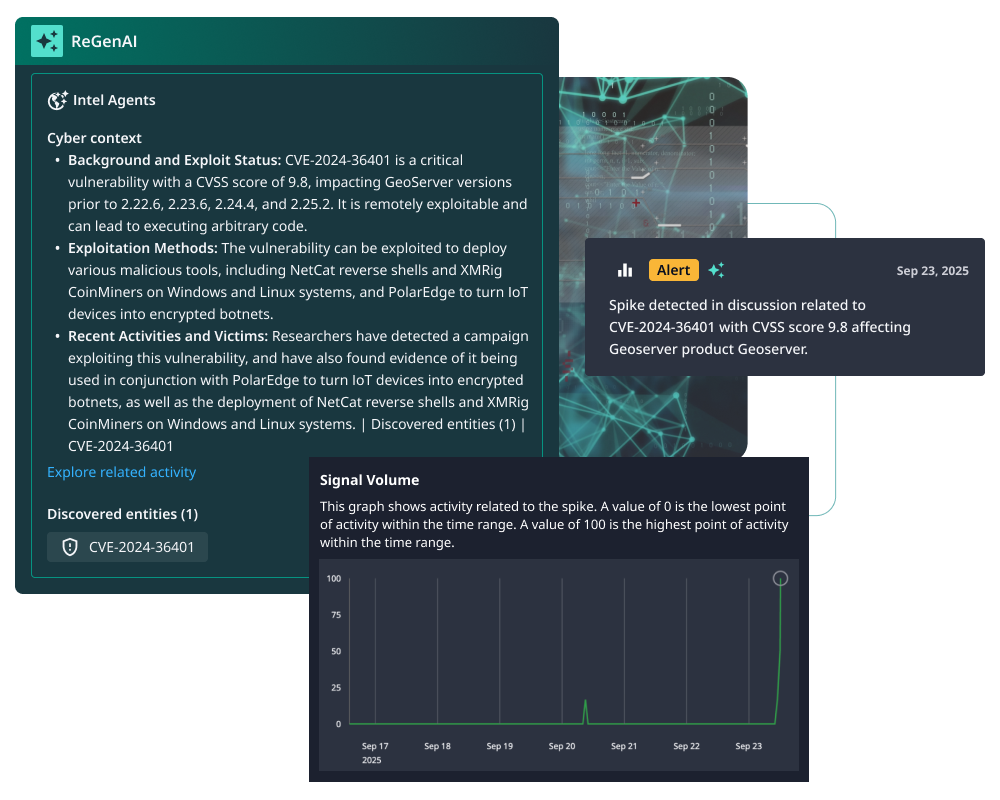
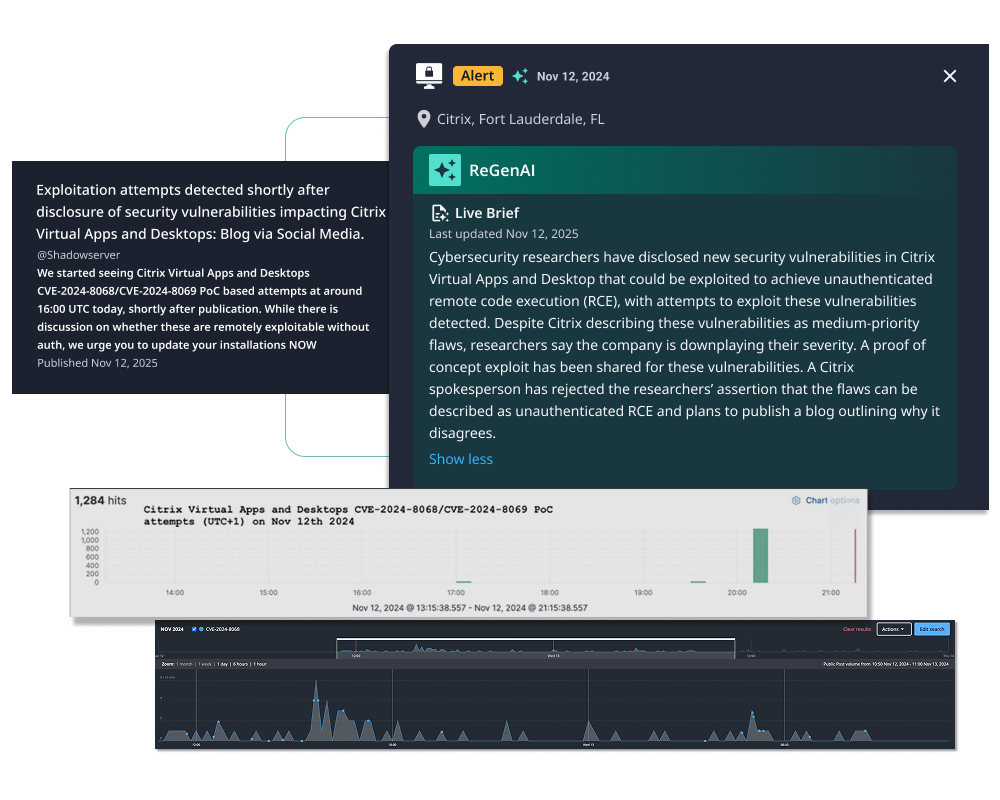
Prioritize, Patch, and Preempt Threats in Confidence
Use Cases
Dataminr delivers foresight against attackers, powering proactive cyber resilience with real-time, actionable intelligence to expose hidden risks and preempt threats beyond the firewall.



Mitigating Third-Party Risk in the Age of Mass Zero-Day Exploitation
- Brad Arkin, Salesforce EVP, Chief Trust Officer
- Mike Kane, Global Payments SVP, Cyber Security Operations
- Brandon Wales, U.S. Cybersecurity & Infrastructure Security Agency (CISA) Executive Director
FAQs
Dataminr’s advanced AI reduces noise through precision tuning, ensuring your team receives highly relevant alerts. You can determine which topics, event types, companies/organizations, and technologies are relevant, giving you granular control over the digital risk intelligence you receive. Additionally, our ReGenAI Live Briefs distill a rapidly-unfolding event into concise, decision-ready information.
No. Dataminr Pulse for Cyber Risk easily integrates with SIEMs, SOARs, and TIPs. For vulnerability prioritization, you can use Dataminr alerts related to software in your tech stack to trigger vulnerability remediation workflows and provide context about the level of risk each vulnerability poses to your organization.
Dataminr has created a revolutionary real-time AI platform for discovering events, threats, and risks in public data. Dataminr is known for pioneering Multi-Modal Fusion AI, which synthesizes text in 150+ languages, images, video, sound and machine-generated sensor data. The company’s world-leading AI platform—powered by more than 50 proprietary LLMs and multi-modal foundation models and trained on Dataminr’s 12+ year proprietary event archive—performs trillions of computations across billions of public data inputs from over 1M unique public data sources on a daily basis.


