Identify Signals of Imminent Cyberattacks

Situation
Fragmented tools and siloed data create blind spots that give attackers opportunities to exploit leaked credentials, exposed systems, and brand assets long before detection. You need a solution that delivers complete external visibility, surfacing emerging risks to your digital assets and footprint before adversaries can act.
Solution
Dataminr processes a broad scope of public data, including the deep and dark web, to identify signals of an imminent attack. Our platform then delivers the actionable intelligence you need to preempt the impact of these threats.
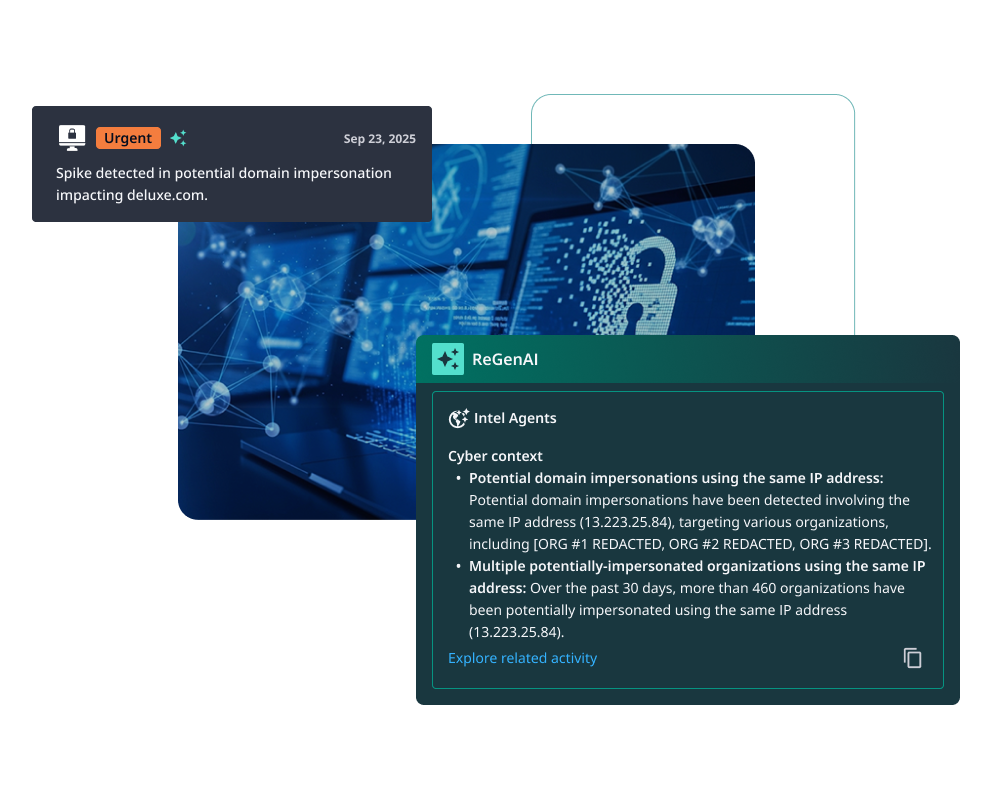
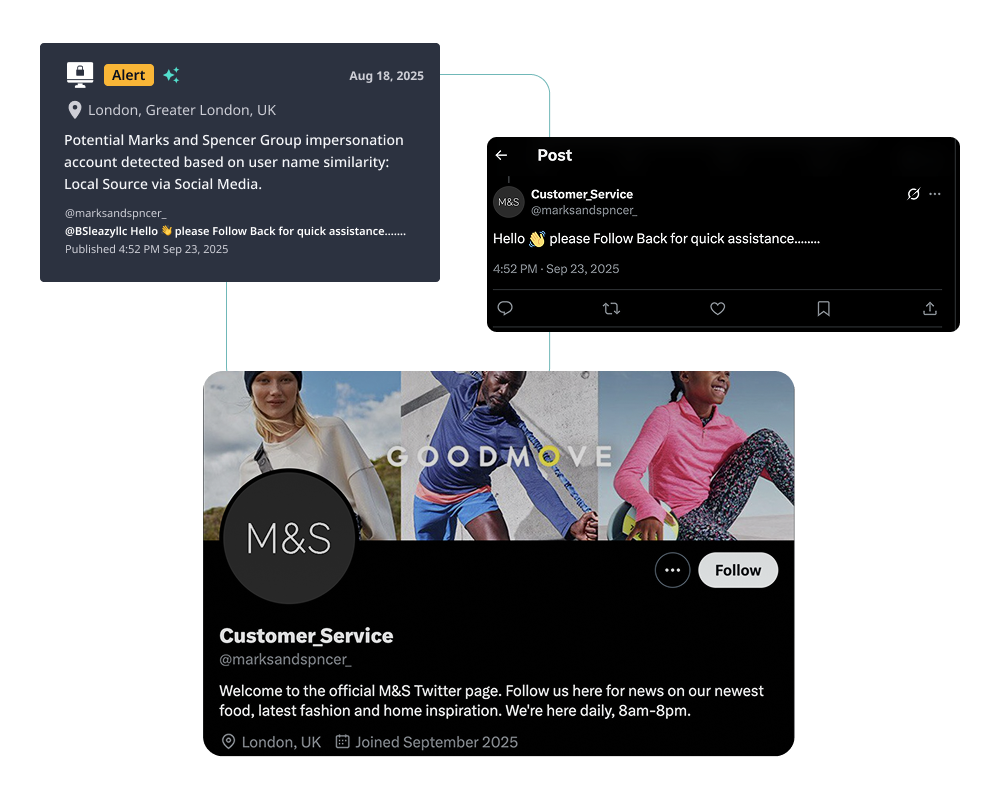
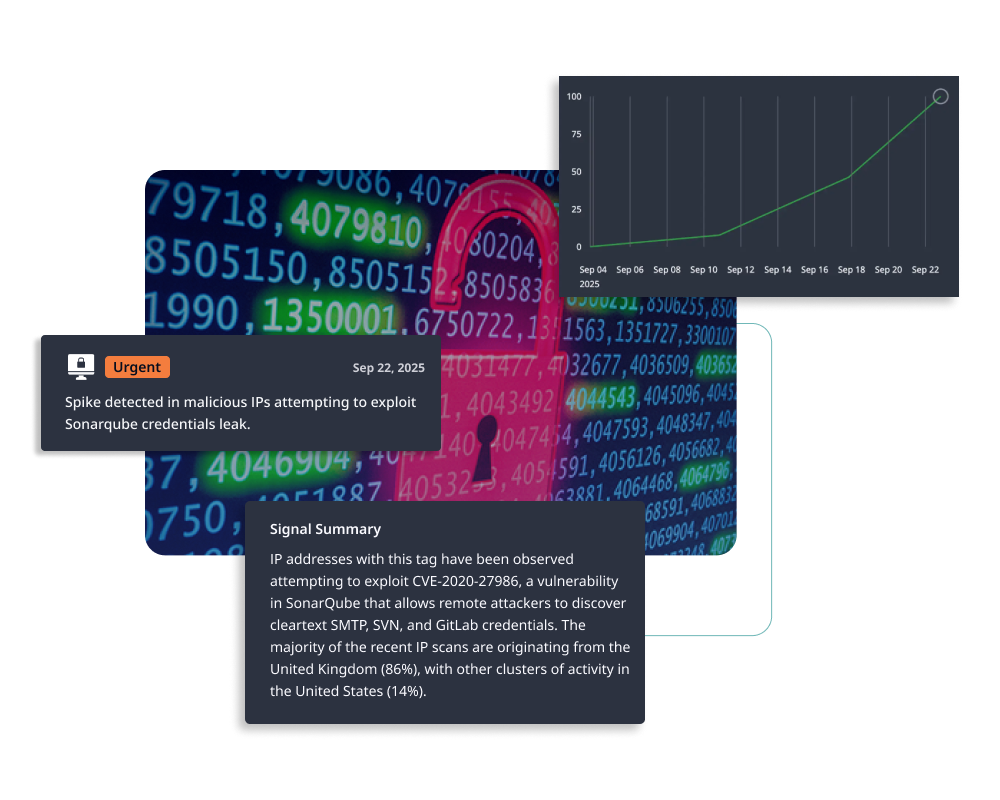
Find Exposures Across Every Medium with Multi-Modal Fusion AI
Eliminate Manual Investigation Cycles with Intel Agents
Use Cases
Dataminr delivers foresight against attackers, powering proactive cyber resilience with real-time, actionable intelligence to expose hidden risks and preempt threats beyond the firewall.



Five Ways to Preempt Cyberattacks with Actionable Intelligence
- Preemptive action is the new frontier in cybersecurity
- Learn to detect cyberattacks instantly using real-time, AI-driven external threat insights
- Diagnose and prioritize escalating, high-risk vulnerabilities and exploits
FAQs
Dataminr’s advanced AI reduces noise through precision tuning, ensuring your team receives highly relevant alerts. You can determine which topics, event types, companies/organizations, and technologies are relevant, giving you granular control over the digital risk intelligence you receive. Additionally, our ReGenAI Live Briefs distill a rapidly-unfolding event into concise, decision-ready information.
No. Dataminr Pulse for Cyber Risk easily integrates with SIEMs and SOARs. For Digital Risk Management, when those platforms are integrated with an IAM system, you can automate processes so that upon receipt of a Dataminr alert indicating an imminent attack on your organization, your IAM can identify sources of compromise within minutes.
Dataminr offers broad deep and dark web coverage, which enables the detection of potential attacks or brand risks on obscure, difficult-to-access forums that traditional domain monitoring tools might miss.
Dataminr has created a revolutionary real-time AI platform for discovering events, threats, and risks in public data. Dataminr is known for pioneering Multi-Modal Fusion AI, which synthesizes text in 150+ languages, images, video, sound and machine-generated sensor data. The company’s world-leading AI platform—powered by more than 50 proprietary LLMs and multi-modal foundation models and trained on Dataminr’s 12+ year proprietary event archive—performs trillions of computations across billions of public data inputs from over 1M unique public data sources on a daily basis.

