Key Takeaways
- Active sale: A threat actor is advertising a “full chain” zero-day exploit for iOS 26 on illicit forums, claiming to possess proof of concept (PoC) code.
- Critical severity: The exploit utilizes memory corruption vulnerabilities to achieve remote code execution (RCE), classifying it as a critical severity threat.
- Remote vector: As a full chain exploit, it likely requires no physical access to the device, relying instead on remote triggers such as malicious web pages or messages.
- Target scope: The exploit specifically targets the iOS 26 operating system, potentially impacting all devices running this version.
Overview of the Vulnerability
Dataminr has detected a credible advertisement for a full chain zero-day exploit targeting Apple’s iOS 26 operating system. The threat actor claims the exploit relies on memory corruption, a class of vulnerability where the software’s memory management is manipulated to execute arbitrary code.
In the context of iOS, a “full chain” exploit is the most dangerous type of mobile threat. It typically combines multiple distinct vulnerabilities to bypass Apple’s layered security defenses:
- Initial entry (Remote Code Execution): Often targeting the WebKit browser engine (Safari) or iMessage, allowing the attacker to run code just by having the victim view a webpage or receive a text.
- Sandbox escape: Breaking out of the restricted application environment where the initial code runs.
- Privilege escalation (Kernel Exploit): Gaining full administrative (root) control over the device, allowing for the installation and use of spyware, keyloggers, or data exfiltration tools.
The threat actor has offered proof of alleged exploit code, increasing the likelihood that this is a viable threat rather than a scam. Successful exploitation would allow an attacker to silently compromise a device, exfiltrate sensitive data (encrypted messages, location, photos), and maintain persistence without the user’s knowledge.
Dataminr’s Detection
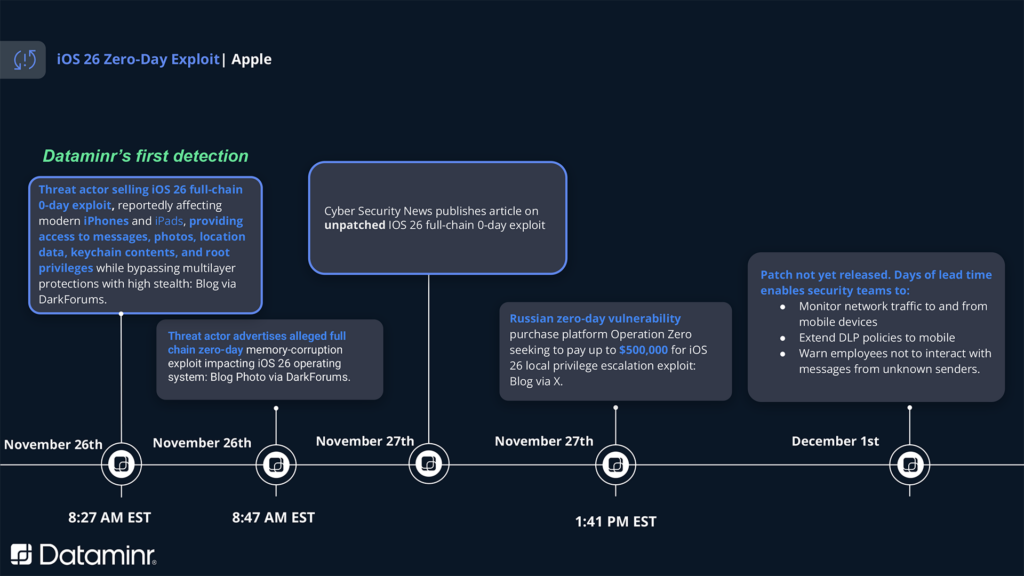
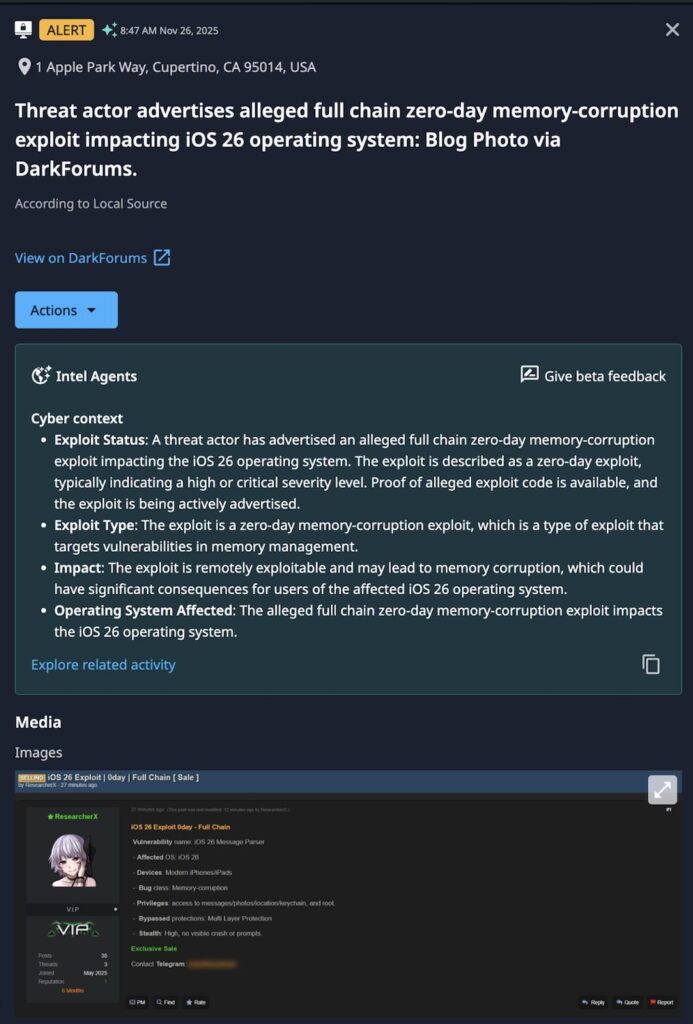
Dataminr’s Recommendations
Organizations should treat this as a critical, active threat until a patch is issued by Apple or the information is proved false.
- Integrate mobile into XDR/SIEM: Employees access sensitive data on their mobile devices just like they do on their laptops and desktops. Make sure your SOC has visibility into risky behavior happening on these devices to ensure an airtight endpoint security posture.
- Monitor mobile traffic: Security teams should monitor for anomalous network traffic originating from mobile devices, specifically large outbound data transfers that could indicate exfiltration.
- Extend DLP policies to mobile: Most data loss prevention (DLP) solutions have the option to flag when a user directly downloads a file to their mobile device. Ensure that this option is enabled to protect against unauthorized data access.
- Enforce patching via MDM: If your organization uses a mobile device management (MDM) solution, minimize the window of vulnerability by enforcing an update as soon as Apple makes it available.

Preempt Breaches with Actionable Vulnerability Prioritization
Discover how Dataminr Pulse for Cyber Risk helps cybersecurity customers evaluate and prioritize vulnerabilities.
Learn More



