Executive Summary
“jrintel” (also known as “JR Intel”) is a financially motivated, high-profile threat actor and information broker who emerged in August 2025. This actor specializes in trafficking sensitive military, intelligence, and government data. Unlike state-sponsored groups that typically align with a single nation’s interests, jrintel acts as a “mercenary broker,” with initial focus on U.S. government and defense contractors, before later expanding focus on a wider range of geopolitical adversaries—including the U.S., China, Russia, Israel, and NATO.
Since late 2025, jrintel has evolved from leaking military schematics to facilitating physical espionage recruitment and selling fraudulent citizenship services, indicating a shift toward a hybrid threat model.
Threat Actor Profile
- Aliases: jrintel, JR Intel, hubz, hubzXjrintel.
- Active since: August 2025 (Joined DarkForums).
- Primary motivation: Financial gain and reputation/clout.
- Modus operandi: The actor acquires high-value data (possibly through supply chain compromises or insider access) and monetizes it via dark web forums and Telegram channels. They frequently release “teaser” documents to verify authenticity before soliciting high-figure sales (e.g., $150,000).
- Forums: Telegram, BreachStars, ReHub, BreachForums
Key Characteristics
jrintel claims to be “trusted” by Chinese and Russian intelligence agencies, yet later evolved to leaking purported sensitive data from the Russian Ministry of Defense and Chinese government agencies. This behavior suggests they are an opportunistic independent broker rather than a state-aligned asset. Based on observed chatter, references to associated chats, and TTPs related to jrintel’s financially motivated activities not focused on espionage, there is a probable connection between jrintel and the predominantly English-language cybercrime ecosystem known as “The Com.” It is also important to note that jrintel actively encourages users on Telegram to inflate their reputation on illicit forums.
Notable Aliases
Dataminr has alerted on four instances between September 16 and October 2, 2025 where the alias “hubz” has been sharing jrintel information on the BreachStars site. The BreachStars account “hubz” previously posted contact information of encrypted messaging platforms that later overlapped with contacts shared by jrintel. In additional Telegram posts, a jrintel account has listed contact information of “@hubzXjrintel”. We believe there is a likely connection between the two different account aliases.
Temporal and Registration Artifacts
Based on analysis of jrintel’s activity patterns, the actor’s operational hours may align with Greenwich Mean Time (GMT). This timezone combined with a registration artifact from a signup to a deep web forum suggests it’s possible the threat actor may be operating from the UK.
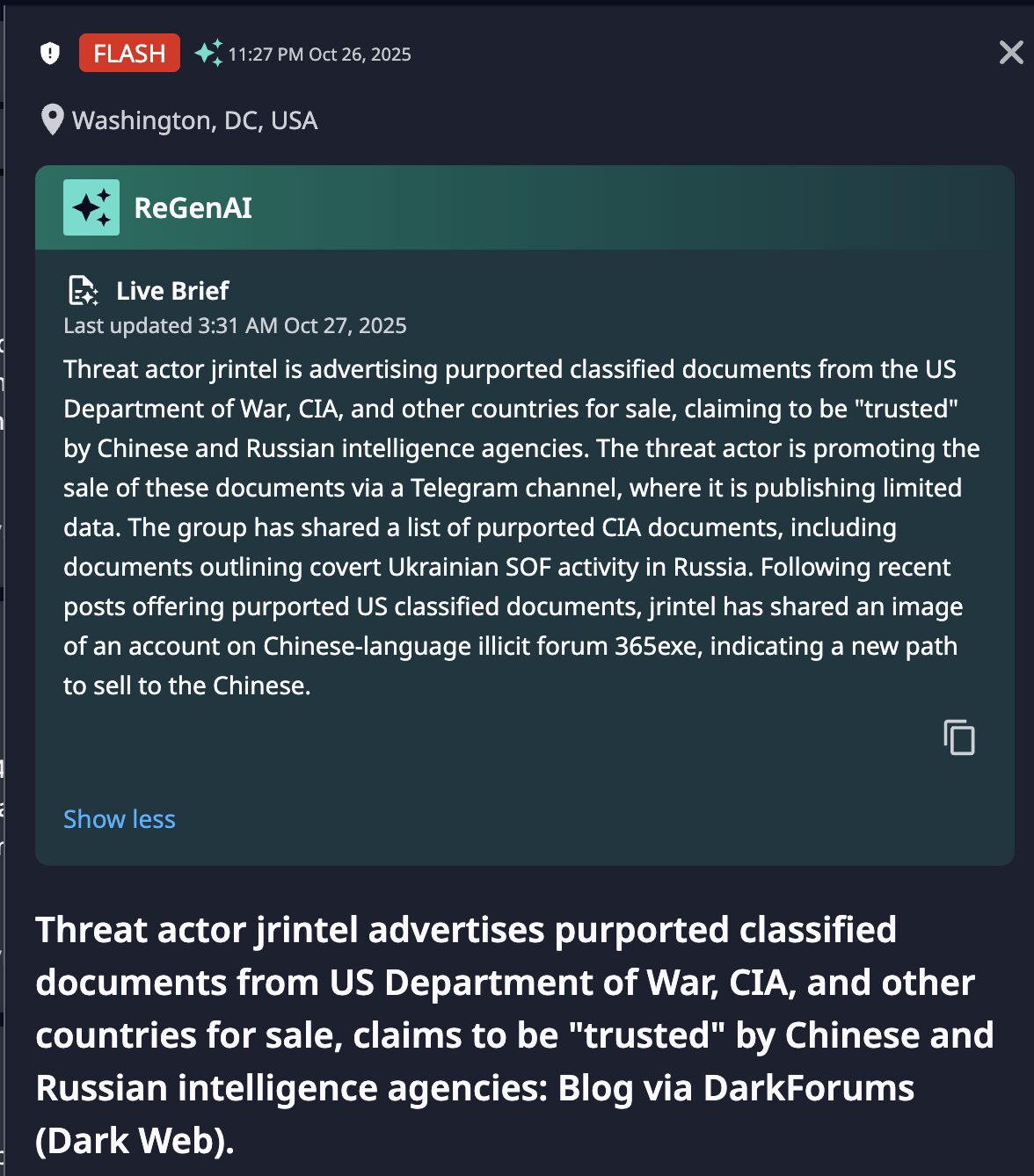
Evolution of Capabilities
The actor’s operations have shifted distinctly over the last six months:
- Phase 1: Military Technical Espionage (August – October 2025)
- Focus: Initially focused on high-tech military hardware.
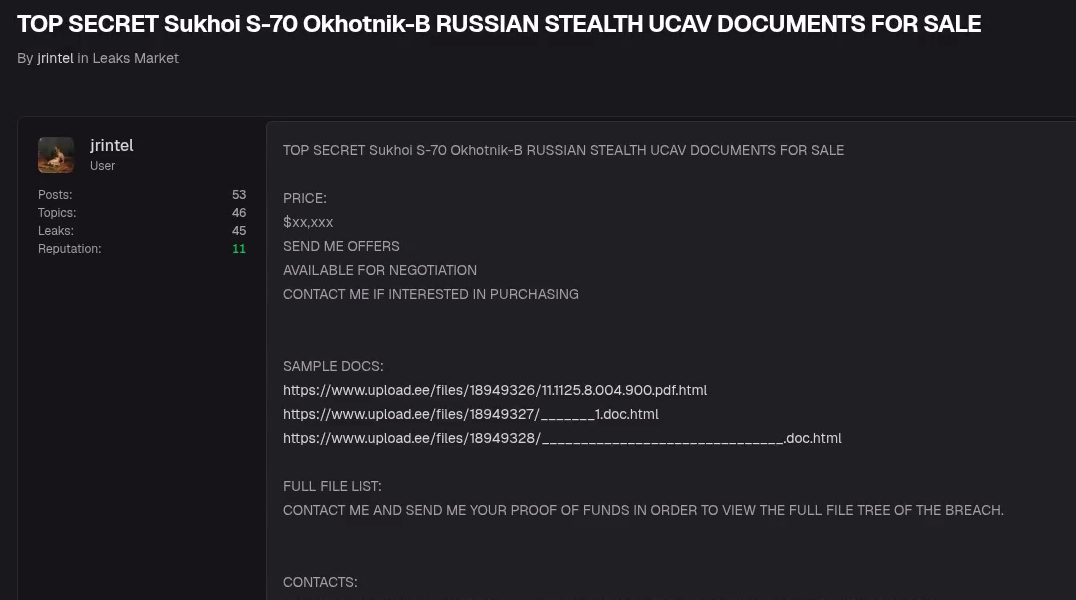
- Notable activity: Published purported schematics for the U.S. Navy Arleigh Burke-class destroyer, Israel’s Barak-8 missile system, SpaceX Raptor engines, and Sukhoi S-70 Okhotnik-B drones.
- Goal: Establishing credibility (“street cred”) within the cybercriminal community by providing authentic, classified “free samples.”

- Phase 2: Broad Intelligence & PII Theft (November – December 2025)
- Focus: Expanded to personal identifiable information (PII) of intelligence agents and large civilian databases.
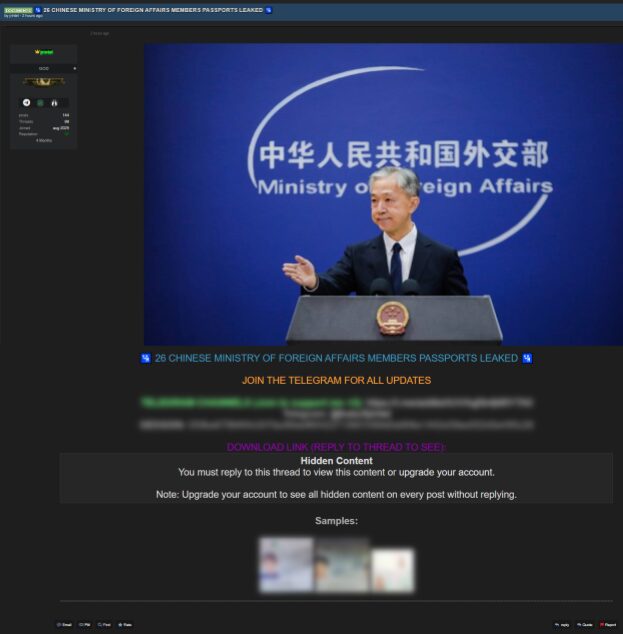
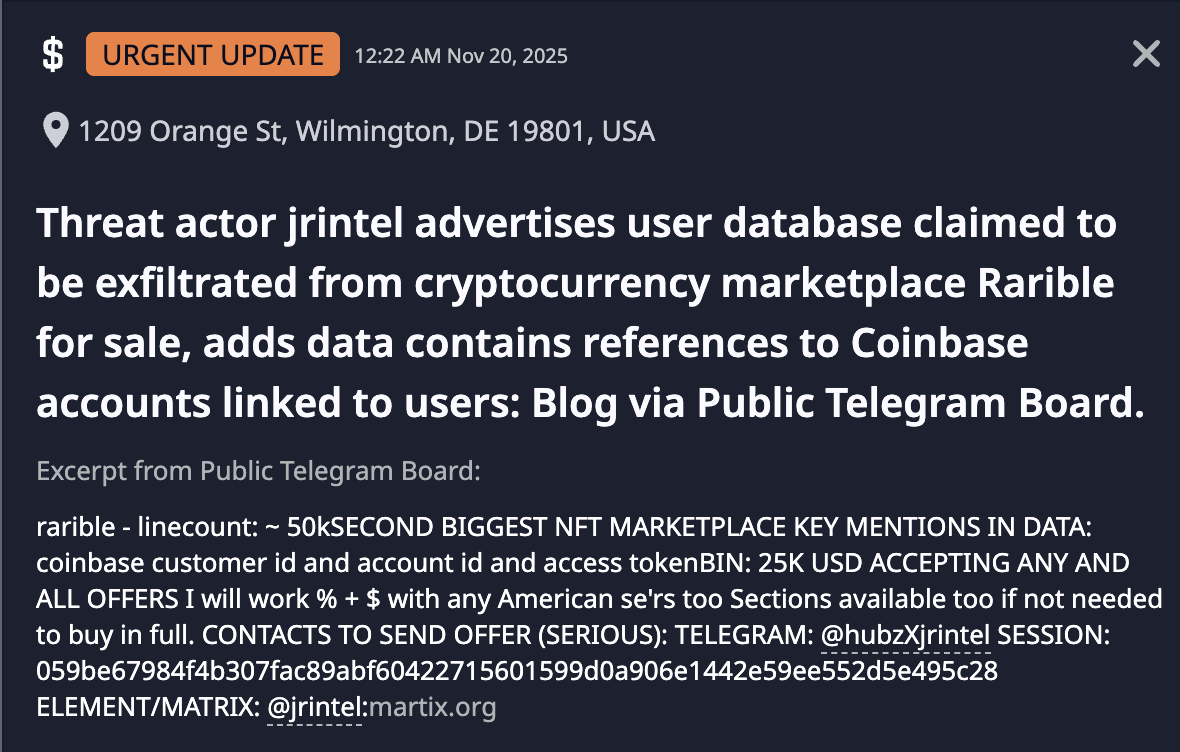
- Notable activity: Leaked purported data related to CIA, MI5, and Mossad agents; advertised a Robinhood Financial database (12M records); attempted to recruit social engineers to leverage compromised data for phishing operations targeting users of cryptocurrency and financial trading platforms; and claimed possession of a database covering all UAE citizens.
- Goal: Maximizing revenue through bulk data sales and high-impact doxxing.
- Phase 3: Hybrid Operations & Services (December 2025 – January 2026)
- Focus: Moving beyond digital theft into physical-world services and “crime-as-a-service.”
- Notable activity:
- Recruitment:
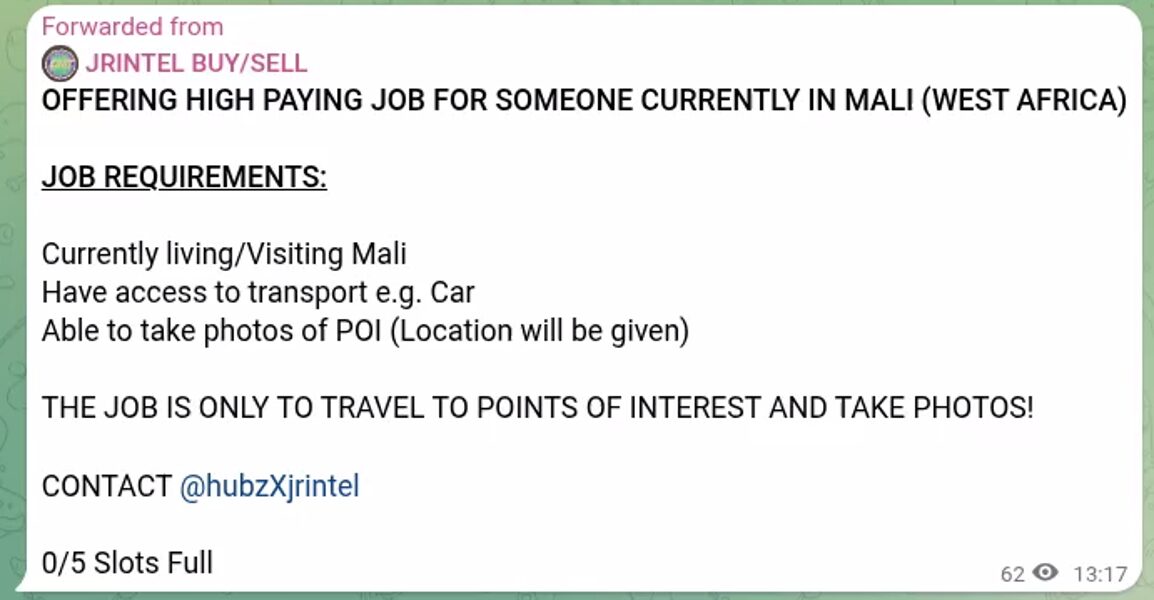
- Posted ad seeking individuals in Mali for physical reconnaissance (taking photos of points of interest). [Caption 1 Image]
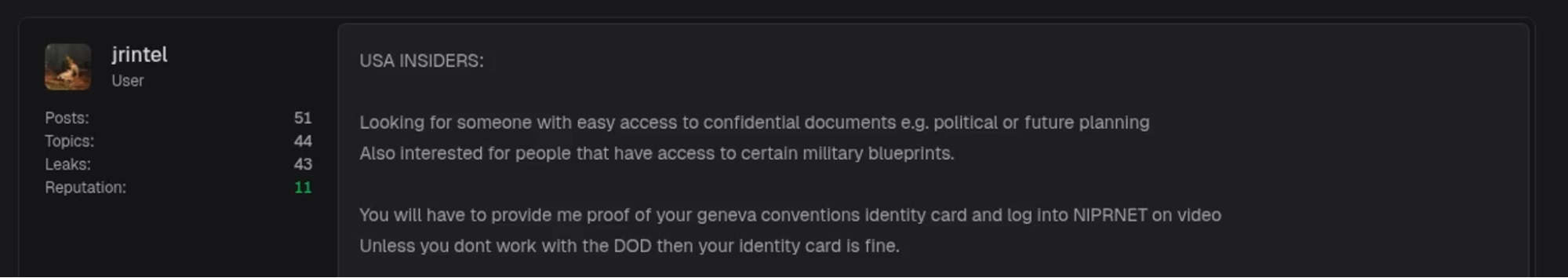
- Post ad seeking U.S. government insider with access to confidential documents or military blueprints [Caption 2 Image]
- Services: Offering fraudulent American citizenship services (starting at $25,000).
- Forum launch: In cooperation with threat actor Renquix, launched new illicit forum.
- Broker wars: Publicly attacking rival brokers (e.g., calling out threat actor “Hasan” for “ruining IntelBroker’s legacy”).
- Forgery overlap:
- Threat actor kitcat, known for advertising a classified documents forgery service, was observed interacting with jrintel on multiple platforms.
- This is worth noting due to lack of third-party corroboration and confirmation for multiple purported documents advertised by jrintel.
- Recruitment:
- Goal: To establish hybrid “Espionage-as-a-Service” ecosystem that merges insider recruitment with cyber and physical espionage, leading to consolidated market dominance.
Tactics, Techniques, and Procedures (TTPs)
Supply Chain Targeting
Frequent targeting of defense contractors (e.g., Lockheed Martin, Raytheon, Thales, PT Len Industri) suggests they exploit third-party vendors to access classified government data.
“Proof of Life” Leaks
Before selling a dataset, jrintel releases 2-5 authentic-appearing documents (e.g., blueprints, passports) on Telegram and forums to prove access.
Cross-Platform Hype
Uses Telegram and dark web forums (BreachForums/DarkForums) to tease breaches, directing buyers to their accounts on encrypted messaging platforms to conduct the actual transaction.
Insider Recruitment
Actively posts job listings for pentesters and insiders (e.g., seeking pentesters for a Chinese gambling site on January 8, 2026).
Diversionary Claims
Makes bold, potentially exaggerated claims (e.g., “trusted by Russian intel”) to obfuscate their true location and origin.
Targeting Analysis
Primary Targets (sectors):
- Defense and aerospace: U.S. Navy, SpaceX, Russian MoD, Thales, Raytheon.
- Government intelligence: CIA, FBI, NSA, MI5, Mossad, China MSS.
- Critical infrastructure: Indonesian Nuclear Power Authority, Italian Customs.
- Civilian data: Robinhood Financial, UAE citizens, Chinese citizens.
Primary Targets (Geography):
jrintel is geographically agnostic, targeting entities in:
- Americas: the United States, Colombia.
- Europe/NATO: UK, France, Italy, Turkey.
- Asia-Pacific: China, Taiwan, India, Indonesia, the Philippines, Thailand, Malaysia.
- Middle East: Israel, UAE.
- Russia/CIS: Russian Federation.
Recommendations for Organizations
To defend against the specific TTPs exhibited by jrintel, organizations, particularly in the Defense Industrial Base (DIB), should implement the following:
- Enhance third-party risk management (TPRM): Since jrintel heavily targets contractors (Thales, Raytheon, etc.), organizations must audit the security posture of their supply chain. Ensure vendors handling classified blueprints have strict data egress controls.
- Monitor dark web and Telegram channels: Proactively monitor channels like “buygovdocs” and forums (BreachForums, DarkForums) for mentions of your organization’s assets or “samples” being leaked.
- Insider threat detection: With jrintel actively recruiting insiders and physical assets, strengthen user and entity behavior analytics (UEBA) monitoring for anomalous data access patterns and unauthorized use of removable media.
- Data leakage prevention (DLP): Implement watermarking on sensitive schematics and documents to trace the source of any leak back to the specific compromised endpoint or user.




