Update (February 12th, 2026)
Recent forensic analysis by Unit 42 has uncovered a significant expansion of the “Lotus Blossom” supply-chain campaign. Beyond the initial scope, investigators identified previously unreported attack infrastructure and confirmed that the threat activity is targeting a much broader geographical and industrial footprint than originally documented.
Expanded Technical & Targeting Details:
- Dual Infection Vectors: The campaign now utilizes two distinct infection chains. In addition to the known DLL side-loading method used to deploy the Chrysalis backdoor, attackers are now deploying a Lua script injection variant. This new method has been observed delivering Cobalt Strike Beacon, granting attackers robust remote command-and-control capabilities.
- Global Reach: The campaign is no longer confined to its original clusters. Confirmed activity now spans South America, the United States, Europe, and Southeast Asia.
- Sector Diversification: Targeted entities now include high-value organizations within the following sectors:
- Government Agencies
- Energy
- Cloud Hosting
- Software Development
- Manufacturing
- Financial Services
Key Takeaways
- Infrastructure Hijacking: Attackers compromised the third-party hosting provider for notepad-plus-plus[.]org rather than the application’s source code.
- Surgical Targeting: The campaign selectively redirected update requests from specific IP addresses to malicious servers to install a trojanized installer that deployed custom malware.
- High-Value Victims: Targeted sectors include Government, Finance, and Telecommunications, primarily in Vietnam, the Philippines, Hong Kong, Taiwan, and Australia.
- CVE-2025-15556: A high-severity (CVSS 7.7) vulnerability in the WinGUp updater allowed unauthenticated remote code execution due to a lack of cryptographic signature verification.
Overview of the Incident
Between June and December 2025, the Chinese state-sponsored threat actor Lotus Blossom (also known as Billbug, Thrip, or Raspberry Typhoon) executed a sophisticated supply-chain attack against Notepad++.
Driven by long-term geopolitical surveillance, Lotus Moon conducts strategic cyber espionage and the systematic theft of intellectual property. The group targets government, defense, and telecommunications sectors primarily in Southeast Asia, though they have recently expanded their footprint into Central America and global open-source ecosystems.
By compromising the project’s shared hosting infrastructure, the actors gained the ability to intercept update requests from the WinGUp (Windows Generic Update Program) mechanism. This was an espionage-focused operation designed to gain footholds on the workstations of developers and system administrators—individuals who typically possess privileged access to corporate networks.
June 2025
Initial Breach
Lotus Blossom gains access to the shared hosting provider for notepad-plus-plus[.]org
July–Oct 2025
Active Redirection
Attackers begin selectively redirecting update traffic to serve the “Chrysalis” backdoor.
Sept 2, 2025
Partial Disruption
Scheduled maintenance by the host removes direct server access, but attackers retain stolen internal credentials.
Nov 18, 2025
Mitigation Starts
v8.8.8 is released, moving update delivery to GitHub to bypass the compromised hosting.
Dec 2, 2025
Access Terminated
The hosting provider definitively kills the attackers’ access and rotates all internal credentials.
Dec 9, 2025
Security Hardening
v8.8.9 is released, enforcing mandatory digital signature verification for all updates.
Feb 2, 2026
Full Disclosure
Technical forensic details and the role of the hosting provider are made public by developer Don Ho.
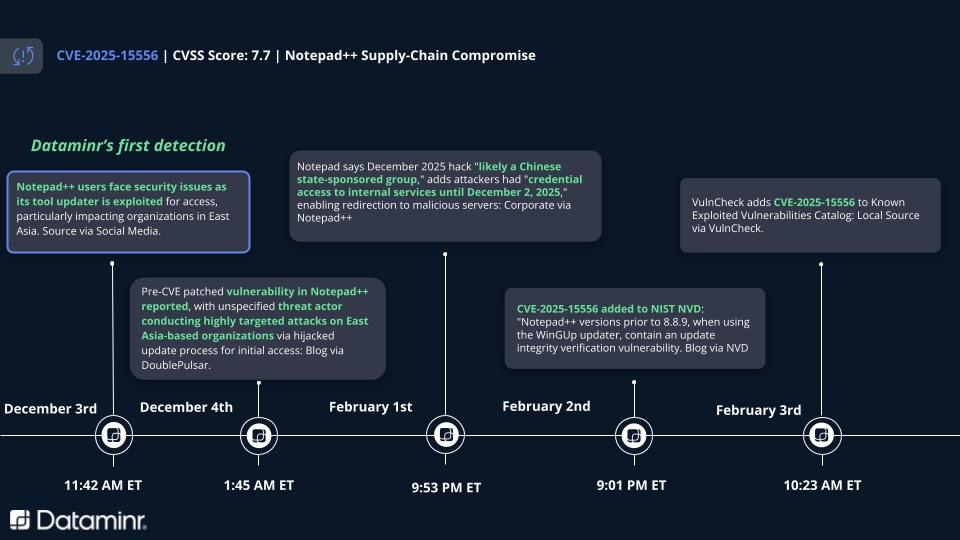
Dataminr Detection Timeline
Dataminr identified initial indicators of the infrastructure compromise 62 days before the official CISA KEV notification. Early alerting allowed organizations a significant lead time to investigate signs of intrusion and harden defenses before the full public disclosure on February 2, 2026.
Technical Details
The vulnerability, CVE-2025-15556, exists in versions prior to 8.8.9. Because the updater did not verify the digital signatures of downloaded metadata or installers, an attacker with network or infrastructure access could force the application to execute a malicious installer with the user’s privileges. The primary payload was Chrysalis, a custom backdoor used for data exfiltration and monitoring communications.
Immediate Actions & Recommendations
- Mandatory Update: Immediately update all instances to Version 8.9.1 or higher. These versions enforce mandatory cryptographic signature verification for all updates.
- Manual Reinstall: For high-risk workstations (e.g., developers in affected regions), do not use the auto-updater. Download the latest version directly from the official GitHub repository to bypass potentially compromised hosting “roads.”
- Threat Hunting: Scan for a process named BluetoothService.exe (a hijacked tool) or unusual child processes spawned by gup.exe or notepad++.exe between June and December 2025.
- Credential Rotation: If a compromise is suspected, rotate all administrative credentials, API keys, and SSH keys used on that machine.

Immediately Detect Signs of Third-Party Breaches
Leverage real-time third-party risk, supply chain, and vulnerability alerting solutions to keep your organization protected.
Learn More