Key Takeaways:
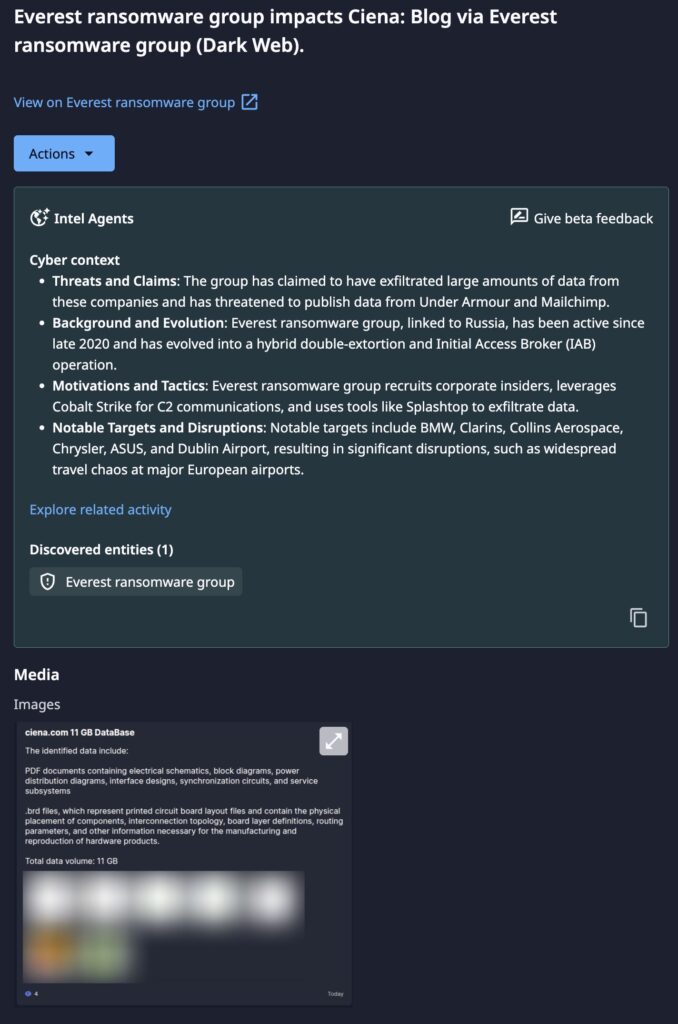
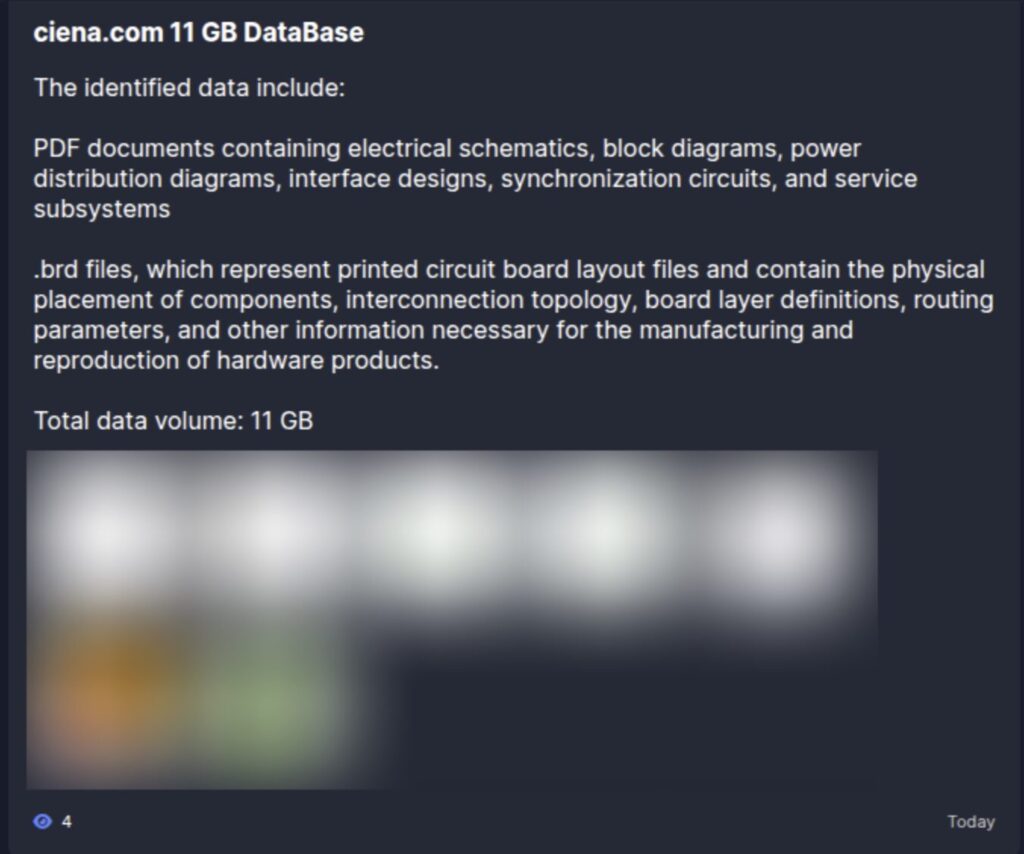
- Critical Data Theft: Everest claims to have exfiltrated 11 GB of sensitive documents, specifically targeting electrical schematics and printed circuit board (PCB) layouts.
- High-Impact Target: Ciena is a cornerstone of the AI ecosystem, providing high-speed optical networking hardware and software essential for AI connectivity.
- Sophisticated Adversary: Everest is a Russian-linked group known for insider recruitment and a hybrid model of double-extortion and initial access brokering.
Overview of the Incident
Dataminr detected an announcement from the Everest ransomware group alleging that it had successfully compromised Ciena Corporation, a leading US-based telecommunications equipment provider. The threat actor claims to have stolen 11 GB of data, which reportedly includes proprietary technical documentation such as electrical schematics and PCB layout files. This breach is particularly significant due to Ciena’s role in developing the high-capacity optical interconnects that enable distributed AI clusters and large-scale AI fabrics.
Everest has a history of targeting high-value infrastructure and manufacturing entities, including Collins Aerospace, ASUS, and Chrysler. Their tactics often involve the use of Cobalt Strike for command and control and Splashtop for data exfiltration. Notably, the group frequently attempts to recruit corporate insiders to gain initial access.
Dataminr Detection
Dataminr’s real-time monitoring of ransomware groups, forums, and channels helps organizations know as soon as they’re potentially impacted by a ransomware attack. It also helps peer organizations know whether their industry or sector could be in the crosshairs of a particular threat actor.
Dataminr’s Recommendations
To protect against attacks from Everest, Dataminr suggest taking the following actions:
- Harden Insider Threat Programs: Implement strict monitoring for anomalous internal activity, as Everest is known to actively recruit corporate insiders for network access.
- Audit Remote Access Tools: Review logs for unauthorized use of tools like Splashtop or Cobalt Strike beacons, which are preferred by this actor for exfiltration and C2.
- Restrict Sensitive Technical Data: Ensure that electrical schematics, PCB layouts, and other critical IP are stored in segmented environments with strict least-privilege access and multi-factor authentication (MFA).
- Monitor for IAB Activity: Everest often functions as an Initial Access Broker; organizations should monitor dark web forums for advertisements of access to their specific infrastructure.
- Supply Chain Review: Partners and customers of Ciena should initiate a risk assessment to determine if the compromised schematics could facilitate future hardware-level attacks or unauthorized cloning of networking equipment.

Get Ahead of Emerging Threat Activity
Proactively adjust your cybersecurity posture based on comprehensive AI-powered real-time threat intelligence.
Learn More