Key takeaways:
- High-Value Data Exposure: Threat actor 888 claims to have exfiltrated the source code for Atlas, a critical financial reporting tool for Microsoft Dynamics, along with private keys and credentials.
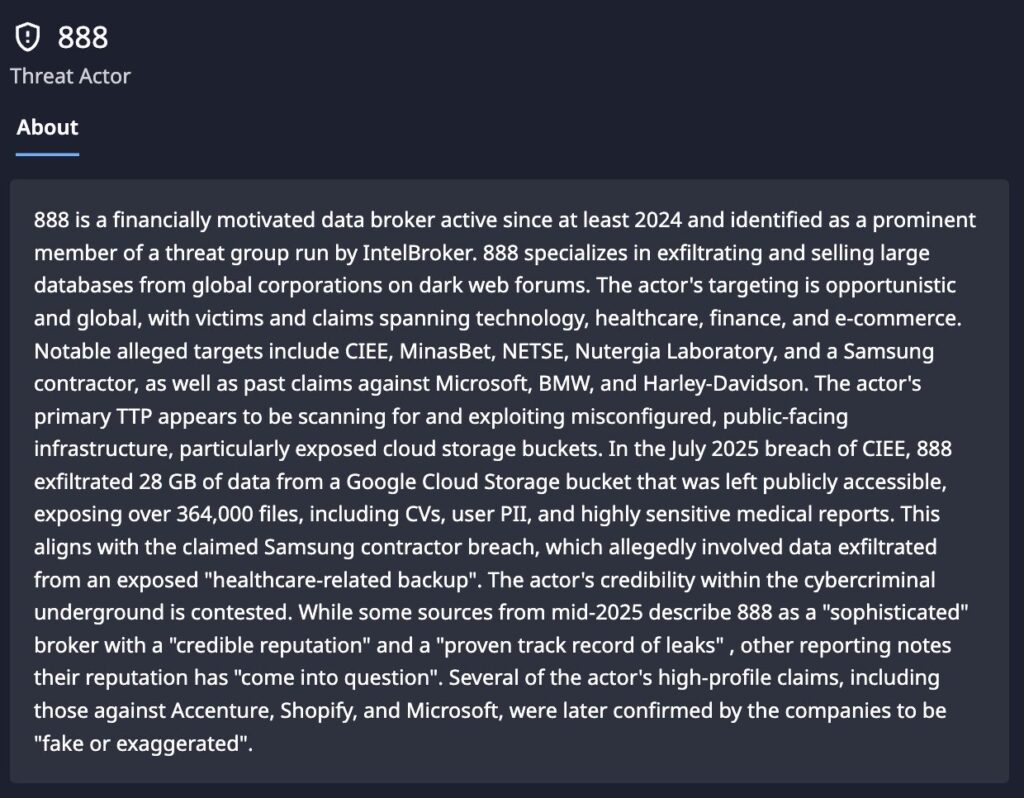
- Verified Threat Actor: 888 is a prominent member of a group previously led by IntelBroker, known for targeting misconfigured cloud infrastructure to exfiltrate sensitive data from major global corporations.
- Supply Chain Risk: The leak of proprietary source code allows adversaries to identify hidden vulnerabilities or logic flaws, potentially leading to downstream attacks on organizations utilizing Insightsoftware products.
- Broad Victimization: 888 has a history of successful attacks against high-profile entities, including Samsung, LG, and HD Hyundai. Dataminr has identified more than 70 attacks in dozens of different countries, underscoring the credibility of 888’s claims.
- Impact: Exposure of customer credentials to third-party systems or compromise of proprietary source code creates a compound, second-order cyber risk that extends well beyond a traditional data breach and greatly increases the potential financial impact.
Overview of the incident:
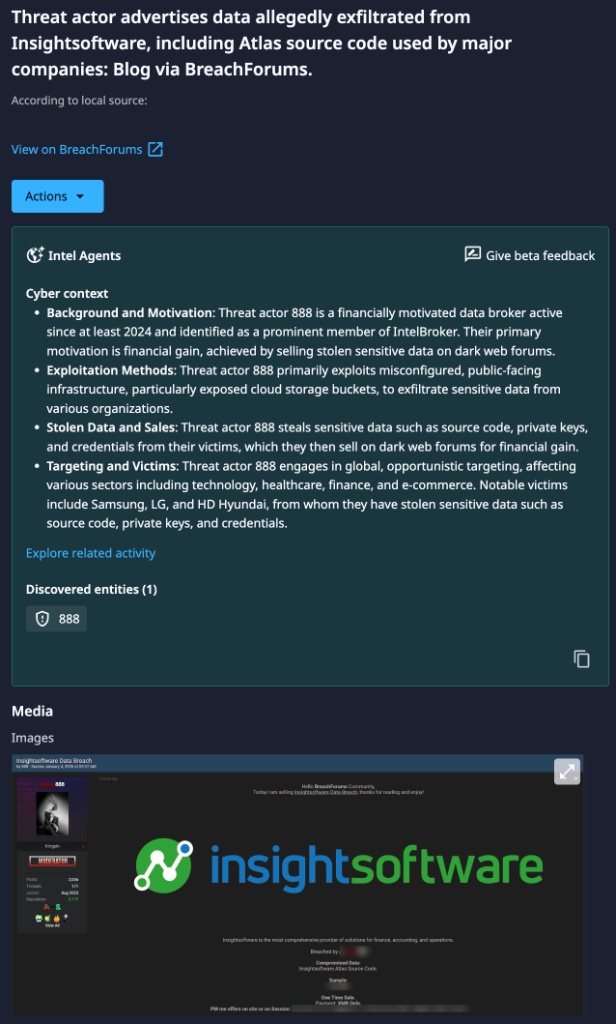
Dataminr detected and alerted on a post on BreachForums where the threat actor 888—a financially motivated data broker and previous associate of IntelBroker—advertised data allegedly stolen from Insightsoftware. The actor claims the breach includes the source code for Atlas, a widely used real-time financial reporting solution for Microsoft Dynamics AX and D365.
Based on previous analysis of known 888 exploitation methods, the exfiltration was likely achieved by exploiting misconfigured, public-facing cloud infrastructure, specifically exposed storage buckets. Beyond source code, the stolen dataset reportedly contains private keys and credentials, which could grant unauthorized access to internal systems or customer environments if these secrets are not immediately rotated.
Dataminr detection
Early detection of this advertisement is critical as it identifies a compromise at the “source” stage of the software supply chain. By alerting organizations before the stolen data is weaponized, Dataminr enables a shift from reactive remediation to proactive risk management.
An incident like this one that results in either exposure of customer credentials to third-party systems or compromise of proprietary source code creates a compound, second-order cyber risk that extends well beyond a traditional data breach.
Exposed credentials to third-party systems primarily risk downstream financial fraud and unauthorized transactions. Data from ThreatConnect Risk Quantifier by Dataminr shows that enterprise organizations with similar access compromises have faced wire and payment fraud ranging from $5M to $50M.
The second phase of this incident—the exfiltration of Atlas source code—risks weaponized zero-day exploits for any customer using the software. This supply chain risk creates hidden exposure, enabling attackers to monitor business logic, authentication, and financial workflows to develop exploits that bypass controls while appearing authorized.
These incidents cause direct losses (fraud, remediation, incident response) and systemic risks: customer loss, regulatory scrutiny, contract disputes, and long-tail exploits. For boards and CFOs, this is a low-frequency, extreme-severity financial risk, with expected loss driven more by high-impact outcomes than just breach response costs.
Dataminr’s Recommendations
Organizations utilizing Insightsoftware products, particularly the Atlas reporting suite, should be sure to take the following four key actions:
- Block updates by implementing the following firewall rule: Deny *[.]insightsoftware[.]com (verify specific update URLs). This action should be taken immediately.
- Audit Logins via Azure AD by filtering sign-ins by App “Atlas” for non-corporate IPs. This action should be taken immediately.
- Freeze write-back in Dynamics by temporarily removing “Write” permissions for the Atlas Security Role. This action should be taken within the first hour.
- Hunt for fraud by reviewing SQL and other logs and querying for changes to Vendor Bank Accounts created via OData/Web Services.This action should be ongoing in the first 24 hours.

Get Ahead of Emerging Threat Activity
Learn more about how Dataminr helps cybersecurity customers get ahead of emerging threats here.
Learn more



