Key Takeaways
- Alleged Microsoft Office zero-day exploit advertised for $300,000 on RAMP by “zeroplayer.”
- Exploit is unconfirmed, but “zeroplayer” has a history of selling legitimate zero-days (WinRAR, WinZip RCEs).
- The exploit reportedly bypasses the Office security sandbox and is likely delivered via a malicious file in a phishing attack.
- Organizations should adopt a “Shields Up” proactive defensive posture focusing on anomalous Microsoft Office activity.
Overview of the Vulnerability
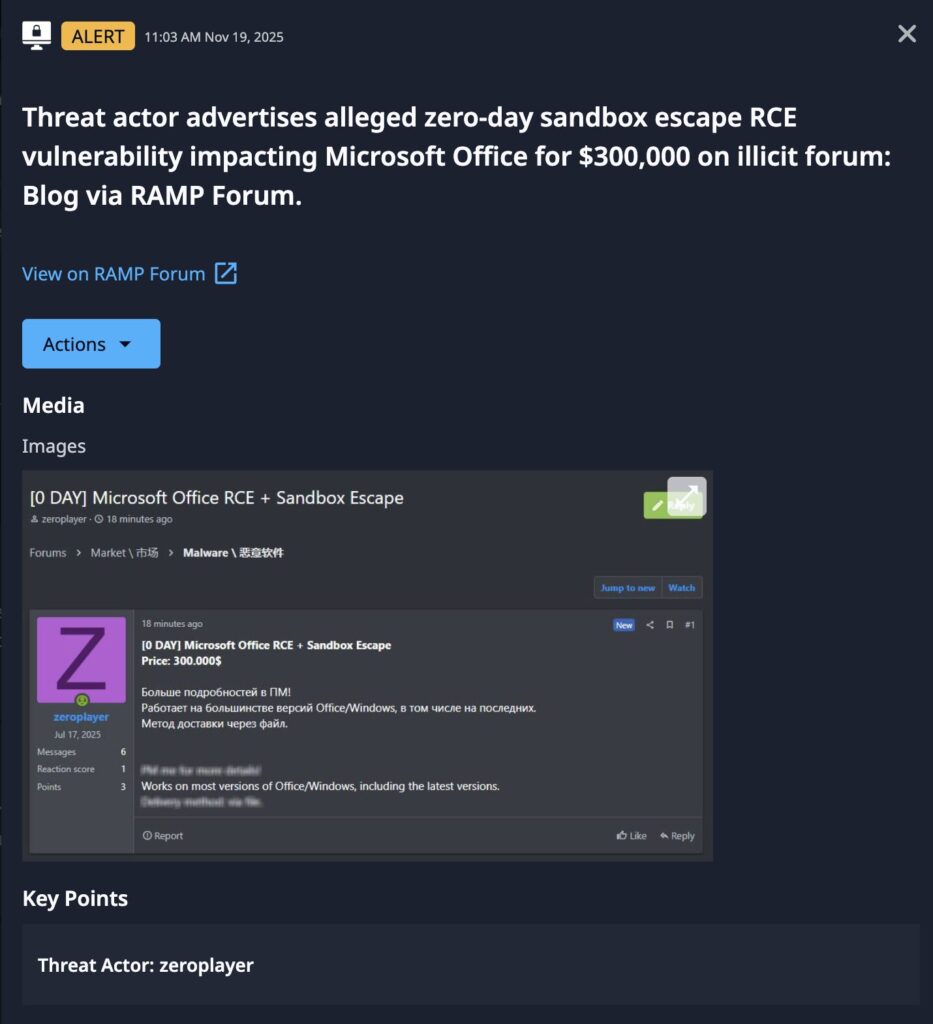
Dataminr Pulse alerted on November 19, 2025, of a threat actor advertising an alleged zero-day exploit targeting Microsoft Office for sale for $300,000 on the Russian cybercrime forum RAMP. While there is not yet evidence of this zero-day, the actor allegedly sold two other legitimate zero-days in the last four months; a WinRAR zero-day remote code execution (RCE) exploit for $80,000 and a WinZip RCE for $100,000. This is reason enough for security teams to operate with extreme awareness around a possible exploit of their Windows Office infrastructure in the near future.
The actor, “zeroplayer,” claims that the exploit works for most versions of Office and would allow the attacker to escape Microsoft Office sandbox, which is a security feature used to isolate malicious code, and compromise the underlying system of the vulnerable device.
They also note that it would be delivered by a file, which implies that whoever purchases and leverages this zero-day would likely embed malicious code into a legitimate-looking Office file (Word, Excel, PowerPoint, etc) that executed in the background if the file was opened. The most successful way to deliver this type of file would be through a phishing attack that leverages social engineering over email, a messaging platform like WhatsApp for Business, or a professional platform like LinkedIn.
Dataminr’s Detection
Dataminr’s Recommendations
Organizations should implement a Shields Up proactive defensive posture with a particular focus on anomalous activity involving Microsoft Office.

Preempt Breaches with Actionable Vulnerability Prioritization
Learn more about how Dataminr helps cybersecurity customers evaluate and prioritize vulnerabilities.
Learn more



