Key Takeaways
- Offensive Powerhouse: Cerberus OS is described as an abandoned private Linux distribution that bundles multiple sophisticated exploitation frameworks and rapid-exploitation tooling.
- NSA-Style Tools: The leak reportedly includes private, high-tier tools comparable to those used by state-sponsored actors, designed for stealth and high-speed compromise.
- Public Availability: The leak occurred on January 2, 2026, on the illicit marketplace BreachForums, making these once-private tools available to a wide range of cybercriminals.
Incident Overview
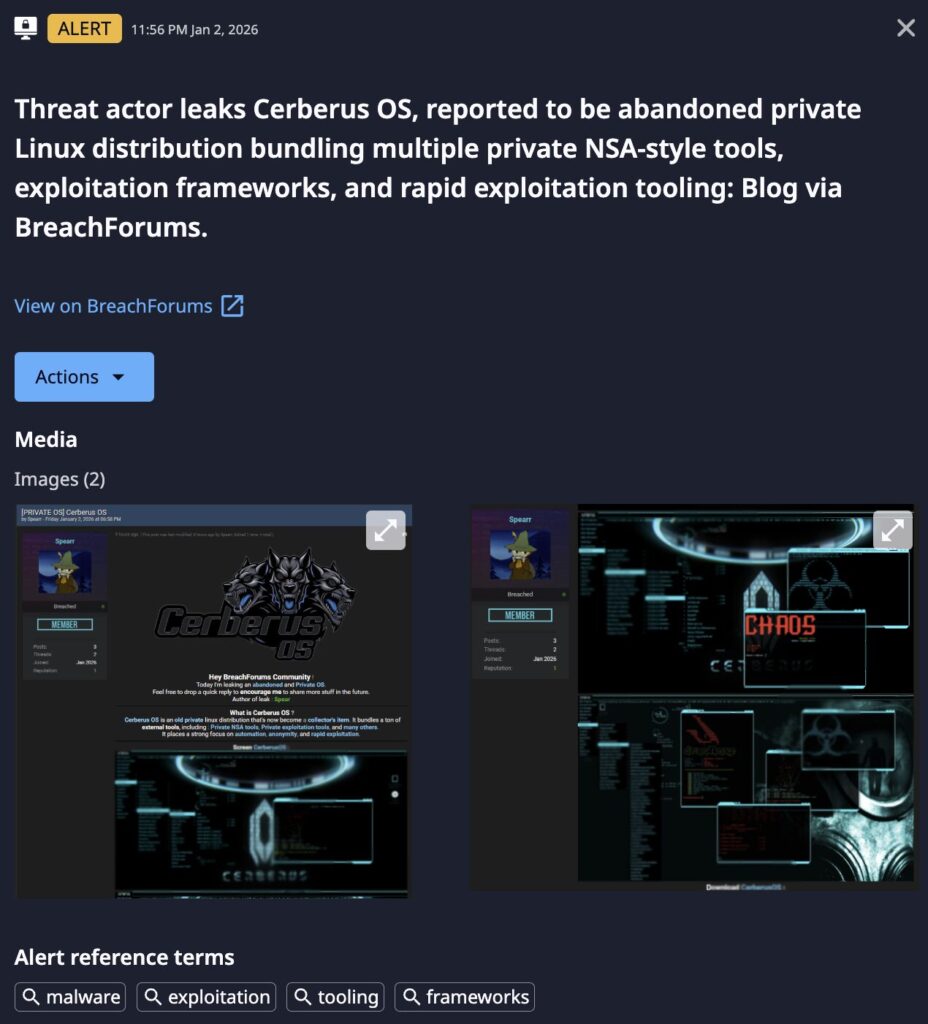
Dataminr detected a significant data leak on the cybercrime forum BreachForums. A threat actor using the alias “Spearr“ published a post containing “Cerberus OS,” also known as “Cerberus Linux,” which they characterized as an abandoned but highly potent pentesting Linux framework.
Originally claimed to be leaked in 2021 by the Bengal Black Diamond gray hat hacking group, Debian-based Cerberus OS is allegedly pre-configured with a suite of “NSA-style” tools tied to the Shadow Brokers leak in April 2017, focusing on automation, anonymity, and rapid exploitation. The distribution reportedly includes custom exploitation frameworks such as Fuzzbunch, Dandespritz, Cobalt Strike, Armitage, the Metasploit framework and Metasploit community version, which allows for the quick identification and compromise of vulnerable infrastructure. The availability of such a specialized framework lowers the barrier to entry for complex attacks, as it provides a ready-made, high-capability environment for conducting offensive operations.
Dataminr Detection
Dataminr’s real-time monitoring of restricted cybercrime forums allowed organizations to be notified of this leak within minutes of its publication. This provides security teams with a critical head start to harden defenses before the tools within Cerberus OS can be widely integrated into active adversary TTPs.
Dataminr’s Recommendations
The release of another powerful automated exploitation framework necessitates a review of the existing security posture against similar tools to ensure coverage. Organizations should focus on identifying the artifacts and behaviors associated with scanning and exploitation which is intended to remain undetected:
- Harden External Surfaces: Immediately prioritize the patching of all internet-facing assets. Frameworks like Cerberus often rely on “n-day” vulnerabilities that have public exploits but remain unpatched in many environments.
- Enhance Behavioral Monitoring: Configure SIEM/EDR solutions to alert on rapid, automated lateral movement or mass scanning activity originating from a single internal node, which is a hallmark of “rapid exploitation” tooling.
- Monitor for Anonymization Tools: Increase scrutiny on inbound and outbound traffic involving known VPNs, Tor exit nodes, or unusual proxy services, as Cerberus OS places a heavy emphasis on attacker anonymity.
- Threat Hunt for Known Tooling: Security teams should proactively hunt for artifacts of common offensive frameworks (e.g., specific staging directories, unique user-agent strings, or default framework certificate signatures) that may be bundled within this OS.

Get Ahead of Emerging Threat Activity
Learn more about how Dataminr helps cybersecurity customers get ahead of emerging threats here.
Learn More