Key Takeaways
- Critical Severity: CVE-2025-55182 is a remote code execution (RCE) vulnerability with a CVSS score of 10.0 affecting React Server Components and Next.js.
- Active Exploitation: The vulnerability is currently being exploited in the wild by multiple APT groups, with proof-of-concept (PoC) code publicly available.
- Unauthenticated Access: Attackers can execute arbitrary JavaScript code on backend servers without requiring any authentication.
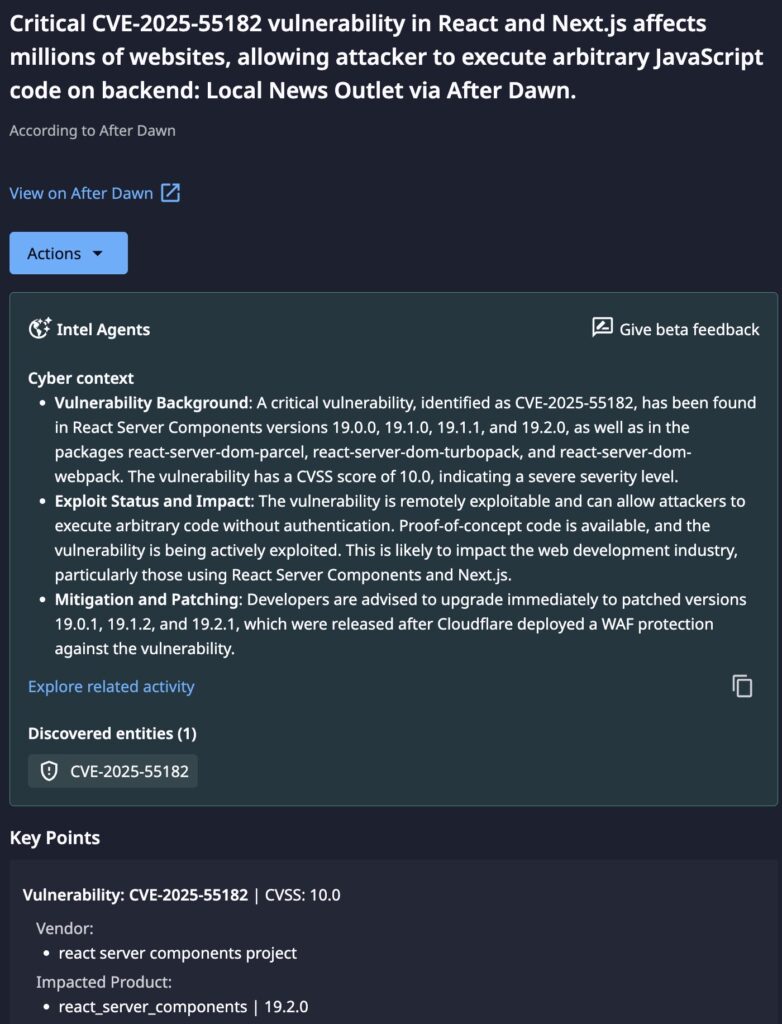
- Immediate Action: Developers must upgrade to 19.2.1 immediately, versions 19.0.1 and 19.1.2 are not patched as previously believed; Cloudflare has deployed WAF protections. In addition, Next.js 15.x, Next.js 16.x, Next.js 14.3.0-canary.77 and later canary releases are also vulnerable and must be upgraded to a patched version; 15.0.5, 15.1.9, 15.2.6, 15.3.6, 15.4.8, 15.5.7, 15.6.0-canary.58, or 16.0.7.
Overview of the Vulnerability
A critical vulnerability, identified as CVE-2025-55182, has been discovered in React Server Components versions 19.0.0, 19.1.0, 19.1.1, and 19.2.0. This flaw specifically impacts packages including react-server-dom-parcel, react-server-dom-turbopack, and react-server-dom-webpack.
The vulnerability holds the highest possible severity rating (CVSS 10.0). It allows a remote, unauthenticated attacker to execute arbitrary JavaScript code on the backend server. This effectively grants the attacker control over the server environment, leading to potential data theft, system compromise, and lateral movement within the network. The issue is particularly widespread as it impacts the web development industry heavily, specifically those utilizing React Server Components and the Next.js framework.
Amazon reported at least two China-nexus APT groups, Earth Lamia and Jackpot Panda, immediately began exploiting React2Shell. Threat actors are using both automated scanners and direct exploitation attempts to compromise organizations, underscoring the severity of the vulnerability and why it is critical organizations upgrade to patched versions.
Dataminr’s Detection
Dataminr identified this critical threat as it broke, providing immediate context regarding the specific vulnerable packages and the existence of active exploitation. This allows organizations to move from “investigation” to “remediation” instantly, reducing the window of exposure for a CVSS 10.0 vulnerability.
Dataminr’s Recommendations
Organizations utilizing React and Next.js frameworks should take the following actions immediately:
- Patch Immediately: Upgrade React Server Components to the identified patched version 19.2.1. This is the only definitive fix. React shared a technical step-by-step for organizations to upgrade successfully. Next.js also shared a technical step-by-step to upgrade to patched versions.
- Deploy WAF Rules: If immediate patching is not possible, ensure Web Application Firewalls (WAF) are updated. Cloudflare has reportedly already deployed protection against this specific vulnerability; ensure similar rules are active in your environment. Amazon shared custom AWS WAF rule as interim protection and Google did as well.
- Audit Backend Logs: Given that the exploit allows for arbitrary code execution, security teams should review backend logs for anomalous JavaScript execution or unexpected outbound connections originating from web servers.
- Verify Supply Chain: Check package.json files across all repositories to identify dependencies on react-server-dom-parcel, react-server-dom-turbopack, or react-server-dom-webpack to ensure no shadow IT or forgotten projects remain vulnerable.

Preempt Breaches with Actionable Vulnerability Intelligence
Discover how Dataminr Pulse for Cyber Risk helps cybersecurity customers evaluate and prioritize vulnerabilities
Learn More



