A majority of chief information security officers (CISOs) agree their role has changed significantly, with 86% noting it’s almost a completely different job than the one they first took on. Today they are facing challenges that extend far beyond the digital realm, and are expected to hone their business sense, operational understanding and leadership skills to help their company thrive.
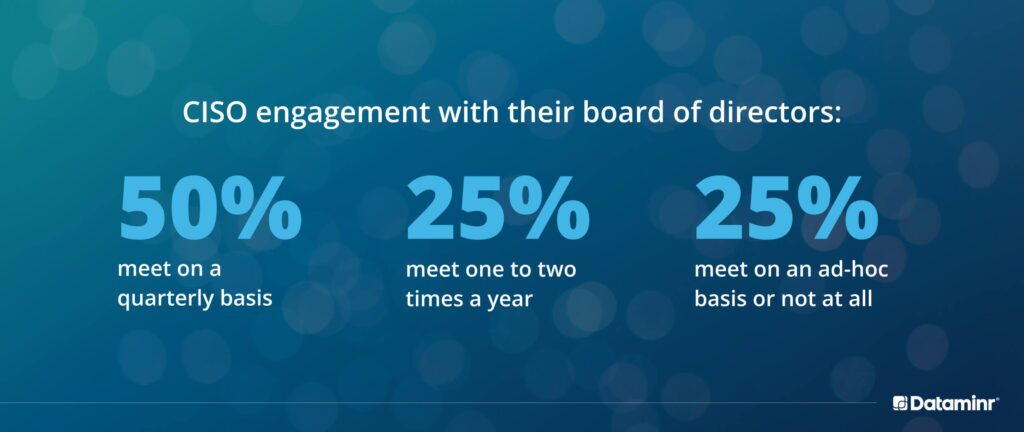
This has given them a seat at the executive table, with 91% of CISOs now having to present to the full board of directors or one of its committees on their organization’s cybersecurity health—whereas before they reported to the CIO and focused primarily on ensuring the security of their organization’s defenses.
In this new role, CISOs are facing greater opportunities, but also the pressure of helping boards understand cybersecurity.
Top 3 board communication challenges
Effectively navigating cyber threats and communicating the value of your team’s strategies can be a difficult task when all parties are not aligned on priorities or how to properly allocate resources.
According to Splunk’s CISO Report, 84% of CISOs say their board or governing body cares more about regulatory compliance than cybersecurity best practices—causing CISOs to walk the line between effectiveness and efficiency. Regulatory compliance can act as a gateway to getting the attention of boards, but it is then up to the CISO to shift the narrative toward prioritizing effectiveness while staying compliant.
Once attention is gained, CISOs are challenged to keep board members engaged:
- Understanding of cyber varies: Technical expertise among board members can vary. One member may have extensive cybersecurity experience while another may not, requiring a CISO to adapt communication styles to have meaningful conversations with the board.
- Informing risk appetite is disconnected: With 88% of S&P 500 companies not having a single cybersecurity expert on their board of directors, stakeholders are often in the dark when it comes to cybersecurity, leaving them unable to understand their organization’s tolerance for risk and blindly making risk-related decisions. This requires CISOs to step in and ensure cybersecurity strategies are properly aligned with their companies’ risk appetite to inform better decision making.
- Gaining attention of distracted stakeholders: At a high level, many executive stakeholders know cybersecurity is a priority. But between finances, product enhancements and more, a board’s attention is splintered, forcing CISOs to compete with other leaders to pull focus, obtain buy-in and gain budget.
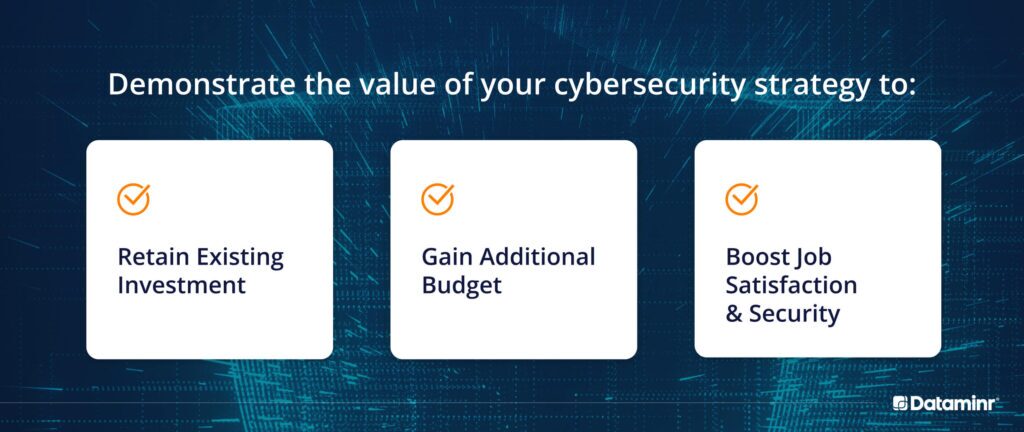
Executive stakeholders are listening. Help them understand.
Ultimately, the board is looking to you for recommendations on what your organization needs to remain both safe and compliant. But executive buy-in is required to implement your strategy. This means advocating for needed procedures and processes in a language that resonates with all board members.
When presenting to the board on a topic as robust as cybersecurity, avoid these five common mistakes:
- Using too much jargon or technical language. Try not to get too into “the weeds” of highly technical workflows, strategies and threat mitigation
- Talking only about successes and ignoring mishaps or areas of improvement
- Forgetting to tie cybersecurity back to overall business health and outcomes
- Including too many statistics, which can overwhelm board members and overshadow data that is most important
- Failing to work closely with fellow business leaders to uncover opportunities for improving business resilience, across all functions, in tandem with cybersecurity best practices.
Communicate more effectively during your next board meeting
Your next board of directors meeting is the opportune time to improve the way you communicate. Begin preparing now to give you and your team the time needed to ensure you are as concise and clear as possible.
The checklist below will help you do so, but first make sure you can answer the three questions your board cares most about:
- What are the implications of both cyber successes and incidents on revenue, overall business health and customer retention?
- What disaster recovery protocols are in place to ensure business continuity and resilience?
- How are competitors and similar companies faring against cyber threats targeting our industry?
Board Presentation Checklist
- Overview of your organization’s cyber strategy and supporting metrics, including critical must-knows and data points
- The average mean time to detect, acknowledge, contain, resolve and recover from a threat/vulnerability
- Response times
- How response times align with regulations and compliance requirements for incident reports
- Current strategy gaps and a plan to remediate deficiencies
- Notable cybersecurity tests such as penetration tests and vulnerability scans deployed to uncover areas of intervention
- The quantifiable impact of cybersecurity programs on business resilience
- The amount of time that has passed since the last high-impact incident
- Consequences if an incident did occur
- Cost of the incident to the company
- Effect of the incident on stock price
- Impact of the incident on brand and reputation
- Impact of the incident on customers
- Potential media coverage and implications on external sentiment
Also key is access to the right data and technology, those that enable you to have the situational awareness needed to do what has become more and more difficult: keep pace with the number, frequency and severity of today’s cyber risks and threats—from geopolitical events and ransomware attacks to cyber-physical threats and sophisticated phishing schemes.
Read More: Most Active Ransomware Groups in 2022-2023
We know that cyber risk is business risk. It’s up to you to ensure that this is fully understood and acted upon by your board and senior management so that your organization can be cyber resilient and drive growth even in the face of a cyber attack or crisis.

Dataminr Pulse for Cyber Risk
Learn how Dataminr Pulse for Cyber Risk arms CISOs with real-time cyber threat intelligence to better understand the threat landscape, and meet the expectations of board members.
Learn More