The volume of cyber threats targeting the expanding enterprise attack surface is increasing significantly. The average number of weekly cyberattacks per organization climbed to an all-time high of 1,876 in the third quarter of 2024—a 75% increase from the same period in 2023. The impact of these threats has become more severe than ever.
Cyber incidents not only disrupt operations, but also carry immense financial, regulatory, and reputational repercussions. This has elevated cyber risks to the top of the C-suite’s agenda, as leaders now recognize that cyber attacks are not just IT issues; they are strategic business challenges.
As the nature and impact of cyber threats evolve, so too does the role of cyber teams which are increasingly seen as drivers of organizational resilience. Leadership now expects cyber teams to provide proactive, timely, and actionable insights to ensure organizations can not only respond effectively to immediate threats but also maintain continuity amidst evolving risks.
Cyber teams are also expected to provide a comprehensive understanding of how cyber threats could impact partners, operations, and the broader organization, helping leadership assess relevance and prioritize their resources effectively. Business leaders increasingly expect cyber teams to maintain a clear, real-time picture of threats. In doing so, they ensure that their organizations are not just reacting to threats but proactively defending against them and fostering resilience.
What is Risk Resilience?
Risk is the likelihood of a negative eventuality, and risk management is the allocation and use of resources to minimize the likelihood and impact of a negative event. Risk itself is a function of three independent variables: threats, vulnerabilities, and the criticality of your assets. Understanding and balancing these variables is critical because some degree of risk is inescapable.
Threat actors have never been more motivated, and their tools have never been more capable. Ransomware continues to be lucrative for criminal organizations. Innovations in criminal practice, such as franchising, and in tooling, such as using large language models (LLMs) for more tailored and effective social engineering attacks, are making the threats more severe. At the same time, a significantly more complicated, more multi-polar, and realigning geopolitical environment has meant more aggression and disruption by state- and state-affiliated actors.
While the threat actors are becoming more capable, a number of developments are impacting the assets, such as the scope and scale of the data cyber teams manage, digital transformation in all sectors, and IT/OT convergence. This means teams are now responsible for more critical digital assets. At the same time, vulnerabilities have increased through significantly expanded attack surfaces. This is the result of many factors including the aforementioned IT/OT convergence, the proliferation of endpoints in recent years, shadow IT environments, and the dramatic expansion of third-party relationships, with 60% of large organizations having more than 1,000 third-party relationships.
Learn More: Webinar Key Takeaways: Third-party Risk in the AI Era
Resilience is the ability to endure and recover from adverse events. In the book, “Cybersecurity First Principles: A Reboot of Strategy and Tactics,” author Rick Howard argues (to lightly paraphrase) that the first principle of cybersecurity is to reduce the probability of a material impact due to a cyber event over a defined period of time. The focus is on the material impact to the organization—rather than attempting to reduce the risk of a cyber event in the abstract.
As a result, businesses should think about resilience in terms of how cybersecurity functions to ensure the resiliency of the larger organization. It requires close coordination with the C-suite and business owners to understand their priorities, and effective communication of risk in terms that these stakeholders and leaders will understand.
Modern risk resilience means recognizing that organizations are in a significantly more challenging risk environment. Because risk is unavoidable and cybersecurity doesn’t exist for its own sake, companies need to align their efforts with key business objectives and think in terms of enterprise risk management, as they work to collaborate and cooperate with other stakeholders. Finally, resiliency today means using the latest technology to solve the identified needs. The attack surface has expanded exponentially, but our resources have not. Organizations need to find reliable automation where they can, which will complement and improve these cyber proficiencies.
The challenge is to manage an organization’s cyber risk posture. Cybersecurity leaders need to make and inform business-relevant decisions under conditions of uncertainty and with limited resources. Decreasing uncertainty is essential to managing cyber risk and an essential part of decreasing uncertainty is finding ways to reduce mean-time-to-detect (MTTD).
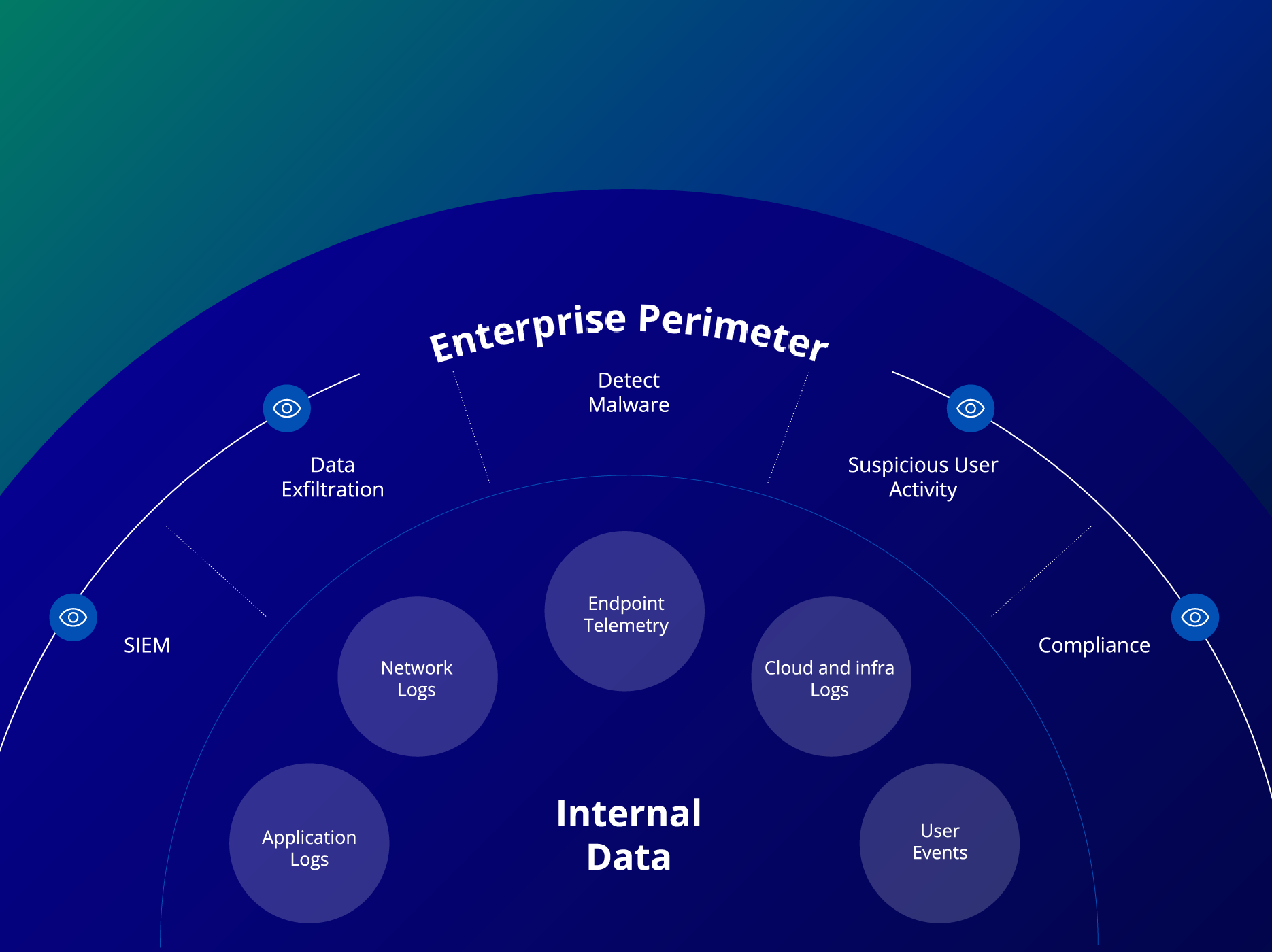
Figure 1: Real-time threat detection inside the perimeter.
Reducing Mean-Time-To-Detect with Public Information
Today, cybersecurity teams dedicate an extraordinary amount of time and resources to continuously monitor their internal systems and data (see FIGURE 1). They monitor endpoints, logs, and user events to detect exfiltration, malware, suspicious behavior, and more. Yet at the same time, cyber teams know that the risk area has expanded substantially and there are risks that can only be detected by looking outside of our perimeter—because either that’s where the threats originate or that may be where teams find the first indication of a threat.
Outside the perimeter, there are millions of data sources producing billions of metadata every day. (see FIGURE 2) This includes sensor data (like Shodan), code repositories (like Bitbucket), regional social media (like Russian VK), global social media (like X), traditional news media, industry blogs and publications, government advisories, disclosures, and the deep and dark web.
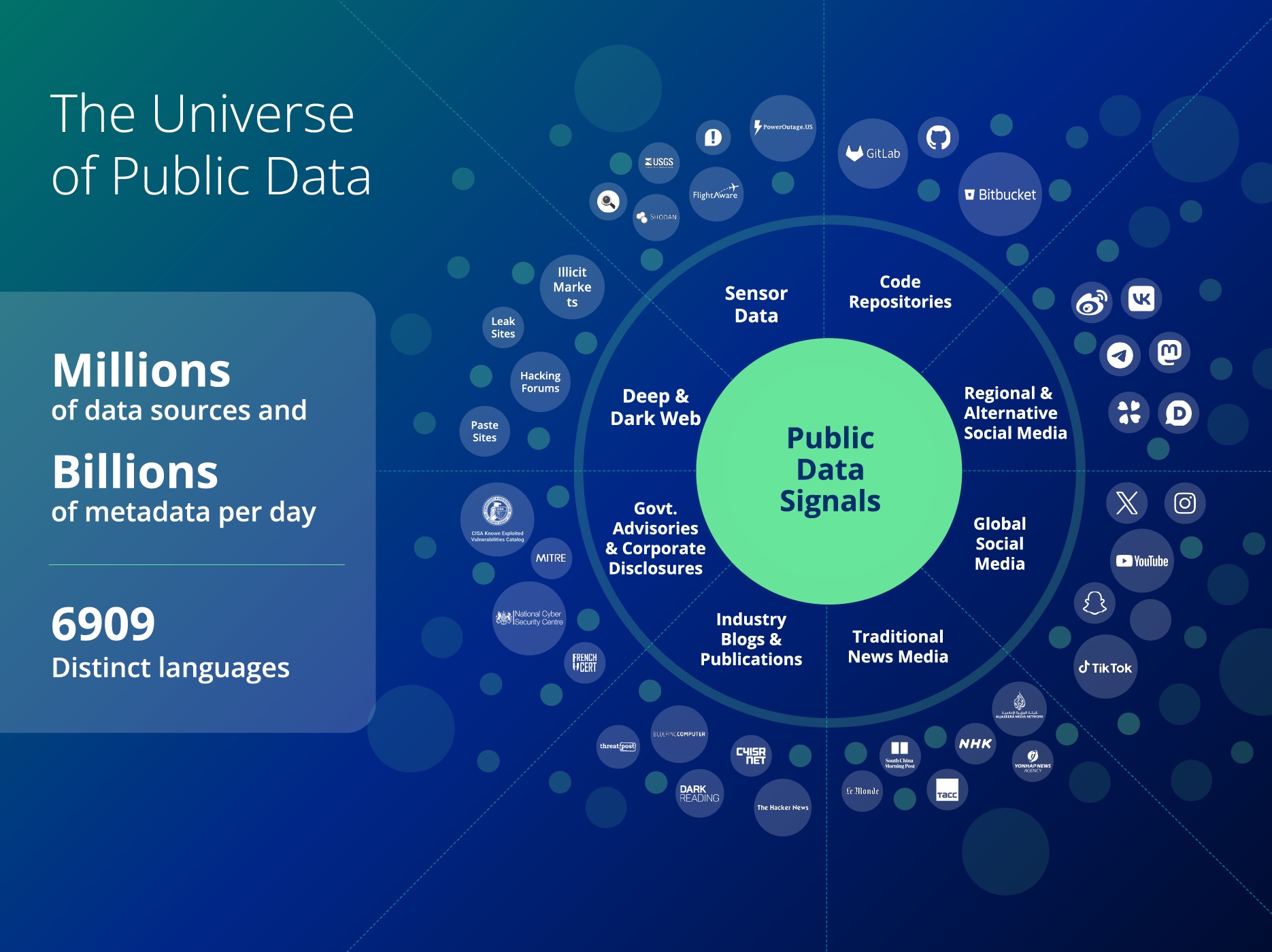
Figure 2: There are millions of public data sources producing billions of metadata every day.
Public data has essential information, but it’s difficult to extract actionable signals in real time. Not only is the scope of the information vast, but those sources are in different modalities including text, images, audio, video, and telemetry data. Additional challenges include distinguishing which sources are credible, determining what’s relevant for your specific operation, how to keep updated on information, and how to ensure you have the latest information.
AI As the Only Solution to the Public Data Challenge
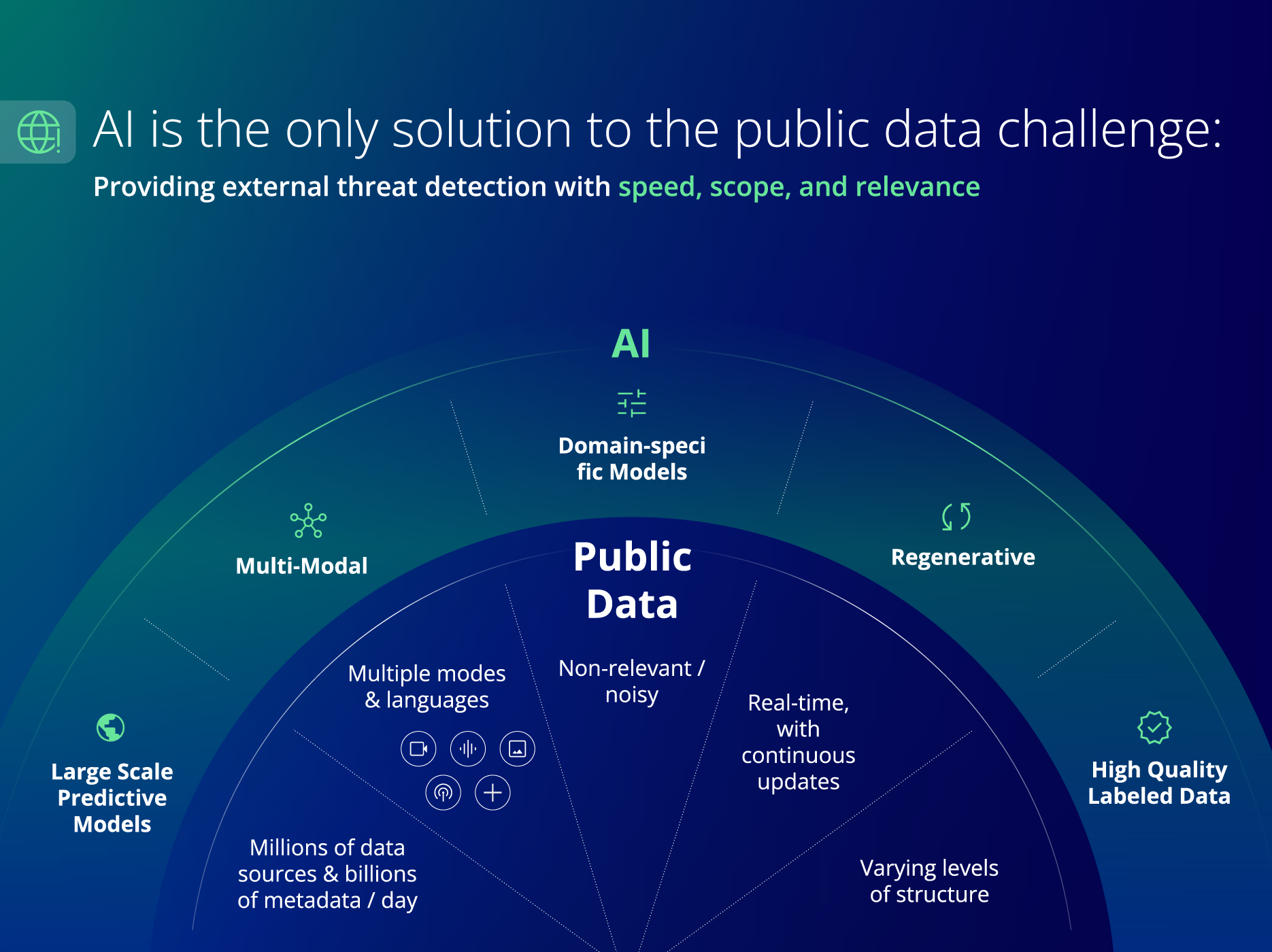
Figure 3: AI is the only solution to the public data challenge.
AI models provide the speed, scope, and relevance necessary to collect, combine, correlate, comprehend, and deliver relevant public information (see FIGURE 3). Large-scale predictive and domain-specific models are able to identify and collect relevant signals. Multimodal models are able to manage different data formats and translate them from different languages. High-quality labeled data verifies and ensures the delivery of reliable, actionable, and normalized signals. Combining generative AI and predictive AI produces regenerative AI, which is able to understand events as they’re unfolding and provide a continuous ongoing summary of events as they arise.
Watch Video: Dataminr Launches ReGenAI
FIGURE 4 illustrates how multi-modal AI helps solve the public data challenge with a general framework. AI models ingest large sets of different data sources in different languages and formats, and extract meaningful signals from those sources. AI then processes and correlates that data to detect potential threats in real-time. The data is scored, tagged, classified, and clustered to detect and evaluate the types of events that require attention.
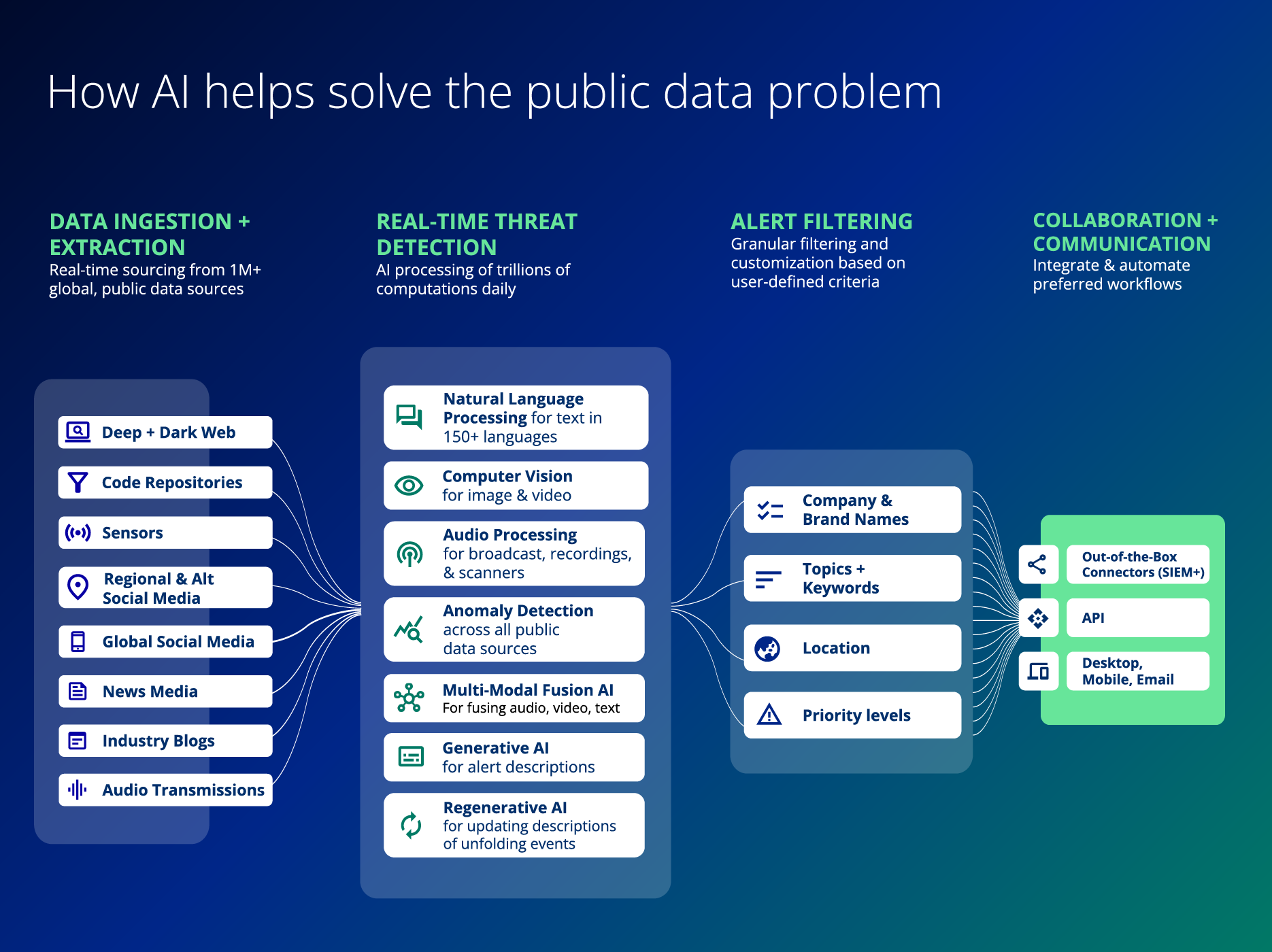
Alert filtering allows you to define how you want to consume this information, for example, by topics, subtopics, keywords, Boolean searches, locations, priority levels, specific companies, and so on. Finally, collaboration and communication integrate and automate preferred workflows with your existing tools.
Real-time threat detection using AI across public data gives cyber teams three distinct advantages:
- Speed: see threats more quickly
- Scope: get comprehensive coverage across geographies and modalities
- Relevance: leverage actionable alerts to reduce uncertainty and drive decisions
Dataminr’s Mission
Our mission is to help security teams take faster actions against emerging risks using publicly available information. This means detecting cybersecurity events in the public domain, recognizing their relevance, and delivering them to the appropriate organization with the appropriate context so that analysts can take the appropriate mitigation actions.

Proactive Defense: Harness Real-time Detection to Disrupt External Cyber Threats
To get more insights into how AI-powered real-time threat detection can help cybersecurity teams uncover hidden threats and disrupt attacks before they occur, watch the full on-demand webinar now.
WATCH ON-DEMAND WEBINAR



