Key Takeaways
- UNC6384 is an active China-affiliated threat actor group with tactics and tools that overlap with known Chinese APT Mustang Panda.
- The attackers use phishing emails containing a malicious attachment that contains malware and provides extensive remote access capabilities.
- Victims are European diplomats from Hungary, Belgium, Italy, and the Netherlands.
- Dataminr has been alerting customers about the zero-day used since March of 2025 and this specific vulnerability since August of 2025.
Overview of the Vulnerability
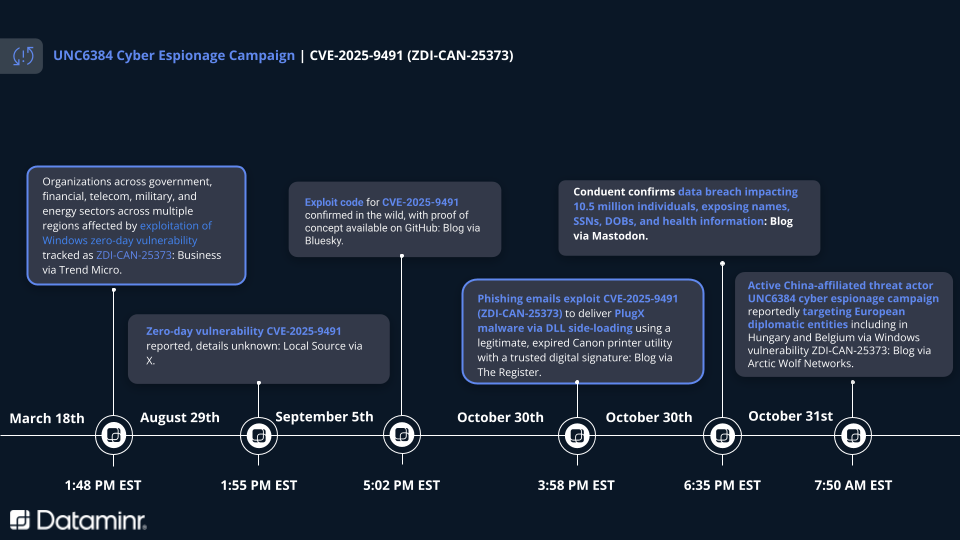
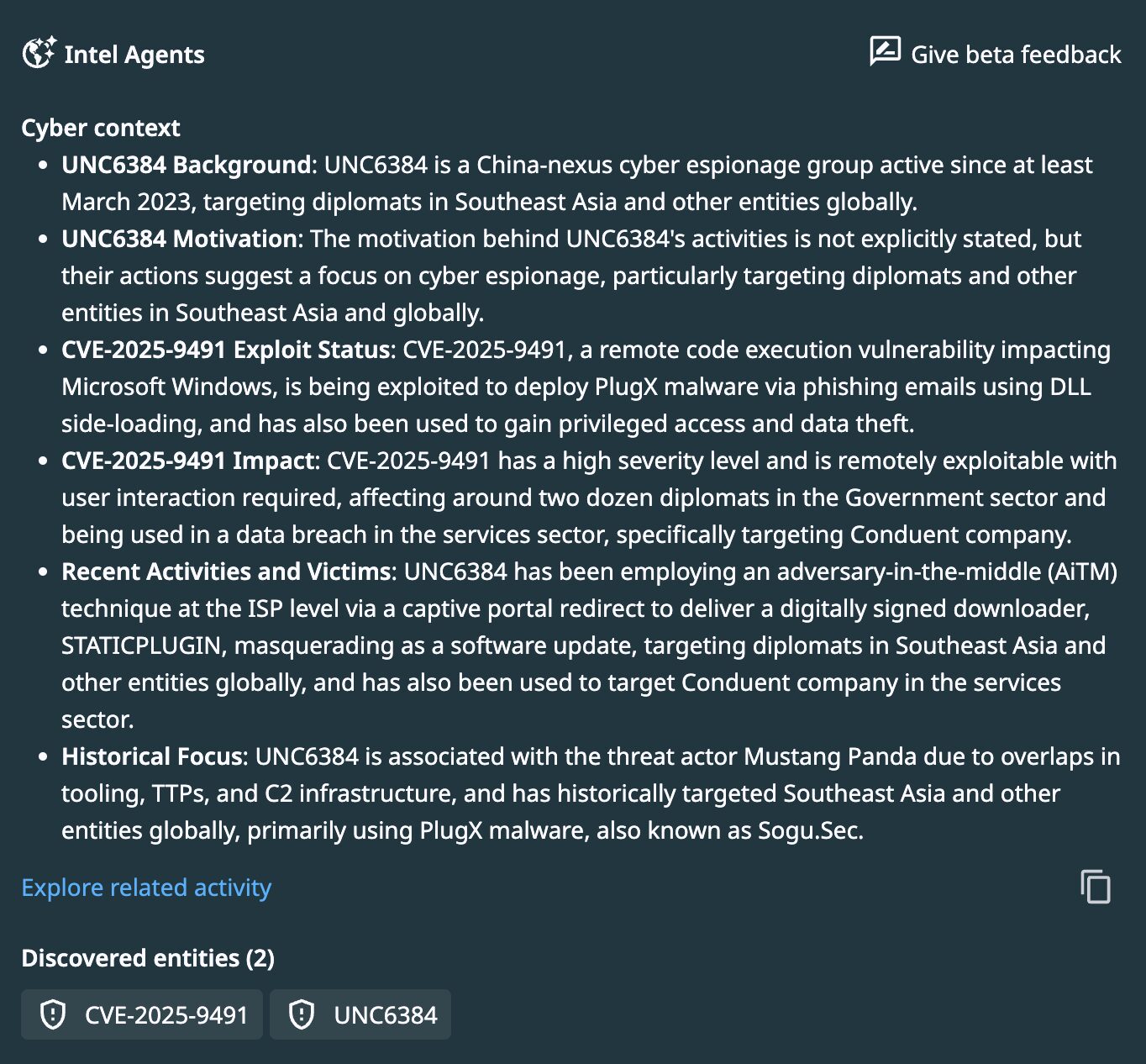
Managed detection and response vendor Arctic Wolf has recently published an in-depth research article detailing how UNC6384, a Chinese threat actor group overlapping with Mustang Panda activity, exploited a vulnerability in Windows to target a handful of European diplomats.
CVE-2025-9491, which was originally tracked as zero-day ZDI-CAN-25373 and potentially used since 2017, is a Windows vulnerability within the handling of .LNK files that allows attackers the ability to remotely execute code following user interaction with a malicious webpage or file.
In this situation, the threat actors exploited the vulnerability by leveraging social engineering to convince their targets to open .LNK attachments within phishing emails that used political lures. Once the target opens the attachments, a decoy PDF document is displayed to the user to make the interaction seem legitimate. However, in the background, the file launches a PowerShell command that extracts a legitimate Canon printing assistant, a malicious DLL that’s sideloaded onto the victim’s device, and an encrypted PlugX payload that is subsequently launched by the DLL.
PlugX is a known remote access tool (RAT) that has been used and continuously developed since 2008. It enables extensive remote access capabilities including but not limited to command execution, keylogging, persistence tactics, reconfunctions, and file upload/download operations.
Dataminr’s Detection
Dataminr’s Recommendations
Vulnerabilities represent critical issues that organizations must build nested defensive responses against. Depending on the vulnerability, that response could range from hardening to patching to searching for potential signs of earlier exploitation in the case of true zero day activity. CVE-2025-9491 has the potential to be particularly challenging in this respect as it appears to have been in use for nearly 8 years prior to disclosure in March 2025.
Organizations can leverage several critical strategies to understand the vulnerability and exploitation landscape, reduce their attack surface and enable detection of post-exploitation activity:
- CVE-2025-9491 was first reported by the Zero Day initiative (ZDI) and alerted by Dataminr in March 2025. Organizations must recognize the threat posed by a vulnerability in core Windows functionality and the timeframe of potential abuse. This will help them search for possible exploitation and plan their remediation.
- CVE-2025-9491 was weaponized as a true zero day prior to disclosure of UNC6384 use. While difficult to defend against, organizations nonetheless can leverage visibility and monitoring of post-exploitation activity (such as installation and use of the long-standing PlugX tool) to identify a breach at relatively early stages.
- CVE-2025-9491 represents an instance of exploitation requiring user interaction. Employee awareness, training, and education can work to inform end users of adversary tradecraft and limit the potential impact of items requiring users to interact with a payload for its successful execution.

Preempt Breaches with Actionable Vulnerability Intelligence
Learn more about how Dataminr helps cybersecurity customers evaluate and prioritize vulnerabilities.
Learn More